0-Day Clickjacking Vulnerabilities Found in Major Password Managers
A Critical Security Alert:
New cyber research exposed stunning 0-day clickjacking vulnerabilities password managers affecting millions of users worldwide. Security researcher Marek Tóth’s groundbreaking discovery confirms that leading password management tools, including market leaders like 1Password, LastPass, and Bitwarden, remain exposed to sophisticated DOM-based clickjacking attacks.
Furthermore, these flaws would allow attackers to steal credentials, two-factor authentication codes, and confidential financial data from unsuspecting users.
What Are DOM-Based Extension Clickjacking Attacks?
DOM-based extension clickjacking is a sophisticated attack channel that exploits how browser extensions are leveraged to interact with web pages. The attack technique also manipulates the Document Object Model (DOM) to trick users into performing unintended actions within their password manager extensions. Tested Research
How the Attack Works
The attack methodology involves several critical steps:
- Overlay Manipulation: Attackers create invisible overlays that hide malicious elements beneath legitimate password manager interfaces
- User Interaction Hijacking: Moreover, when users attempt to interact with their password manager, they unknowingly trigger malicious actions
- Data Extraction: Subsequently, sensitive information becomes accessible to cybercriminals through these manipulated interactions
Affected Password Managers and Current Status
The leading vendors, including 1Password, Bitwarden, LastPass, iCloud Passwords, Enpass, and LogMeOnce, are still in danger until August 2025 and represent around 32.7 million active installations at risk.
Vulnerability Response Status
The response from affected companies varies significantly:
Non-Responsive Vendors:
- LogMeOnce: Failed to respond to security researchers’ outreach attempts
- 1Password and LastPass: Classified the vulnerability reports as “informative,” indicating no immediate plans for remediation.
Active Response Vendors:
- Bitwarden: Currently developing fixes for identified vulnerabilities
- Enpass: Working on comprehensive security patches
- iCloud Passwords: Apple is actively addressing the security concerns
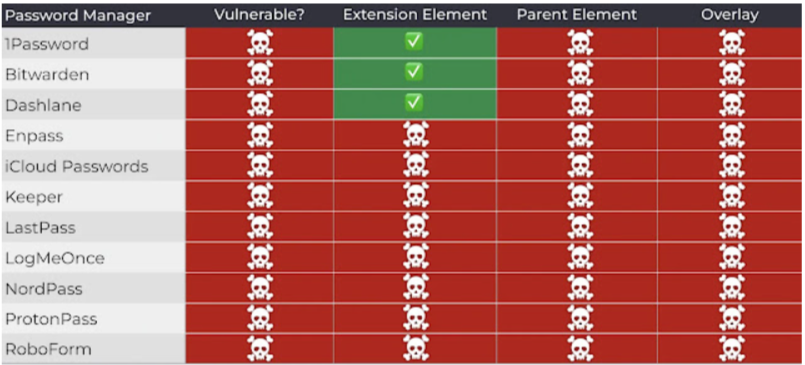
However, major players, including 1Password, Bitwarden, LastPass, iCloud Passwords, Enpass, and LogMeOnce, remain vulnerable as of August 2025, representing approximately 32.7 million active installations still at risk.
The persistence of these vulnerabilities in widely used password managers highlights the complexity of securing browser extensions against sophisticated client-side attacks.
Technical Analysis of 0-Day Clickjacking Vulnerabilities Password Managers
Attack Vector Information
Popular web browser password manager extensions have been found susceptible to clickjacking security vulnerabilities, which could be exploited to hijack account data, 2FA codes, and credit card numbers in certain scenarios.
The technological innovation of such attacks is that they can:
- Bypass regular security controls that are implemented using password manager add-ons
- Leverage the established trust between users and their password management software
- And move quietly without triggering standard security alarms
Risk Assessment
The 0-day clickjacking bugs that were found present a number of severe threats:
- Credential Compromise: Stored usernames and passwords are retrieved directly
- Financial data theft: Bank account information and credit card disclosure
- Multi-Factor Authentication Bypass: 2FA codes and token interception
- Cross-Platform Exploitation: Flaws occur across several browser platforms
Impact on Cybersecurity Landscape
User Trust Implications
The revelations of these loopholes have a big effect on user trust in password management software. As a result, organizations and individuals that trust these tools for online security are exposed to unprecedented threats.
Industry Response Requirements
Information security experts emphasize the need for:
Instant Patch Creation: Rapid security update release
Enhanced Testing Procedures: Tighter vulnerability testing procedures
User Communication: Unambiguous disclosure of security threats and mitigations
Mitigation Strategies and Best Practices
Immediate User Actions
Meanwhile, the users can also implement various protective measures:
- Browser Extension Updates: Regularly update and install available security updates
- Multi-Layered Security: Use extra authentication measures beyond and above password managers
- Suspicious Activity Monitoring: Moreover, check account access history and suspicious login activity periodically.
Organizational Security Controls
Enterprise users should consider:
- Security Test: Conduct extensive penetration testing to discover vulnerable systems
- Policy Updates: Revise security policies to include password manager vulnerabilities
- Employee Training: To train employees on potential clickjacking attack vectors
How OraSec Can Help Protect Your Organization
Companies interested in 0-day clickjacking vulnerabilities password managers can avail themselves of professional security evaluation services. OraSec, a top-rated penetration testing firm, provides advanced vulnerability evaluation solutions that assist in detecting and removing security threats prior to their becoming major issues.
OraSec’s Penetration Testing Services
OraSec’s expert penetration testing team provides:
- Expert-led vulnerability assessments to uncover hidden security risks
- Comprehensive security reports with actionable remediation insights
- Tailored security solutions designed to address specific organizational vulnerabilities
- Regulatory compliance support ensuring adherence to industry security standards
Conclusion
The 0-day clickjacking revelations of password manager flaws remind us in a healthy way that even our strongest security defenses can contain perilous flaws. With more than 32 million users exposed, the security community needs to make remediation a priority and institute stronger security controls. Companies and individuals must right away evaluate their use of password managers, institute extra security protocols, and look into professional vulnerability testing.
In addition, the cybersecurity community needs to learn a lesson from this attack to make future security deployments stronger and secure users from such threats. For businesses that need full-service security testing services, seasoned penetration testing firms such as OraSec are the ones that bring the expertise to detect and remediate vulnerabilities before they become serious security incidents.
