What Is Phishing-as-a-Service (PhaaS) and How to Protect Against It
Cyber threats are evolving at a very rapid rate, and one of the most concerning trends in the past few years is Phishing-as-a-Service (PhaaS). This pay-as-you-go service has revolutionized the approach to making phishing attacks by cybercriminals, and even low-capacity actors can now have access to sophisticated cyber threats. Furthermore, awareness of PhaaS is critical for organizations to protect themselves from these now-too-prevalent attacks.
Understanding Phishing-as-a-Service (PhaaS)
Phishing-as-a-Service (PhaaS) is an emerging, dangerous trend in cybercrime business models. Additionally, it is a pay-per-use model that enables cybercriminals to outsource their phishing services to skilled vendors. Like legitimate Software-as-a-Service (SaaS) platforms, PhaaS vendors provide end-to-end platforms and services that are specifically crafted to enable phishing attacks.
The PhaaS model functions exactly like any other standard cloud service. The platforms are also subscribed to by cybercriminals for an annual or a monthly subscription charge, which provides them with pre-configured phishing kits, hosting platforms, and technical assistance. The platforms greatly reduce the entry barrier for cybercrime, and it is very easy for consumers with less technical expertise to carry out sophisticated attacks.
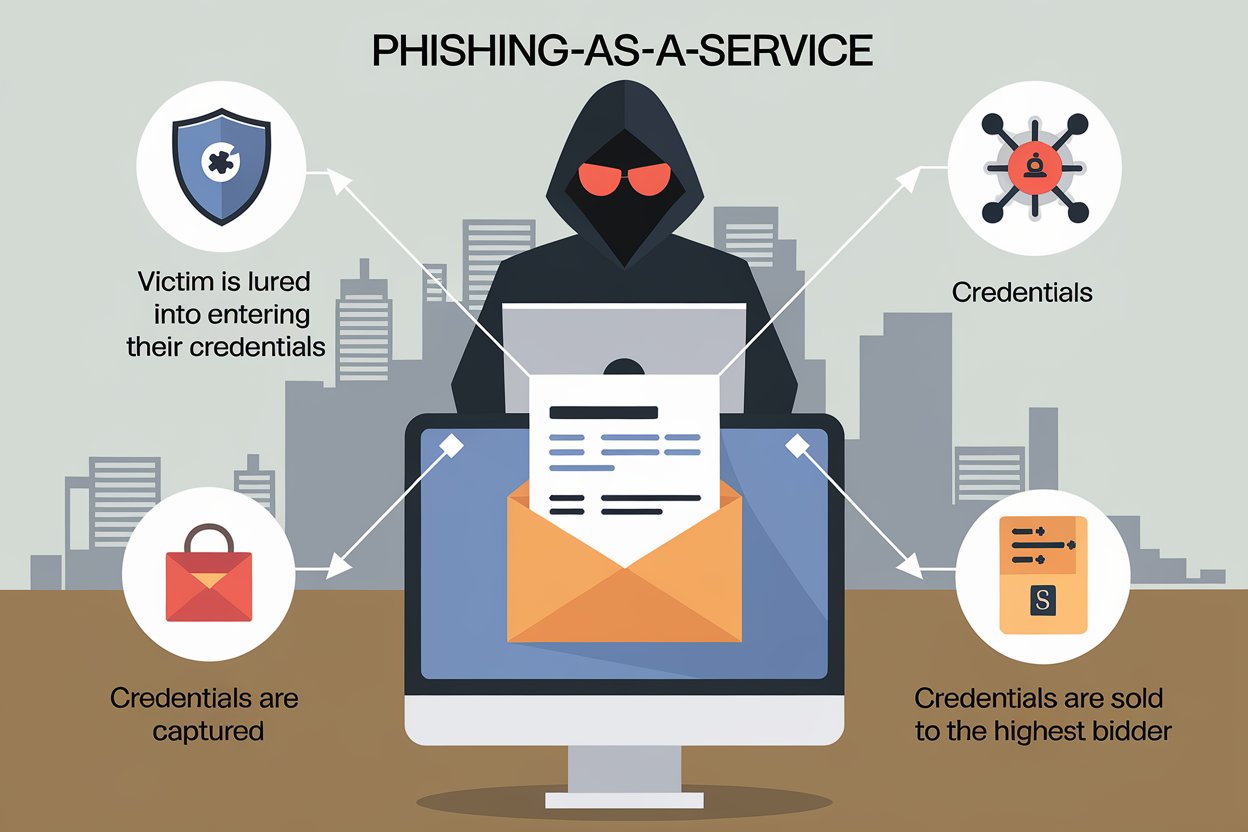
How Phishing-as-a-Service Operates
The PhaaS platform operates using many key components that harmoniously work together. First, service providers design and host advanced phishing websites with website replication features, email templates, and hosting infrastructure. Second, the sites typically have simple interfaces that make it convenient to initiate attacks to the extent of choosing targets and clicking on buttons.
Most PhaaS platforms offer the following services:
- Pre-formatted phishing templates that mimic popular brands
- Automated email delivery systems
- Real-time credential harvesting dashboards
- Sites that keep changing their domains in order to evade detection
- Customer support and tutorials for new users
Moreover, most PhaaS providers keep on developing their services to remain one step ahead of security. They keep on updating fresh templates, enhancing evasion methods, and integrating artificial intelligence to make the forged content even more genuine.
The Growing Threat Landscape
Current statistics point out the rising trend of phishing-as-a-service attacks. According to a study by Barracuda, around 30% of credential attacks in 2024 were found to be detected by using PhaaS kits, and the rate is predicted to grow to 50% by 2025. Additionally, phishing attacks also grew by 61% in six months, largely because of Phishing-as-a-Service maturity.
The availability of PhaaS platforms has democratized cybercrime. In the past, deploying advanced phishing campaigns needed high technical skills and resources. PhaaS has, however, removed these impediments and made it possible for anyone with malicious intentions to buy prepackaged attack tools from the dark web.
A number of prominent PhaaS platforms now command a significant portion of the threat market. Tycoon 2FA represents 89% of all PhaaS cases, while EvilProxy has 8% and Sneaky 2FA has 3%. These platforms have also been evolving and incorporating sophisticated features such as multi-factor authentication bypass capabilities.
Popular PhaaS Platforms and Their Capabilities
Tycoon 2FA
Tycoon 2FA is the most sophisticated PhaaS platform in existence today. It is meant to evade two-factor authentication by hijacking session cookies rather than just credentials. Additionally, its effectiveness has made it the most utilized among cybercriminals.
Darcula PhaaS v3
Darcula v3 automates phishing kit building, which allows attackers to duplicate any site in minutes. The platform is the leader in automated phishing technology, with the ability to deploy realistic-looking clone sites quickly.
EvilProxy and Sneaky 2FA
These websites offer other techniques for credential theft, each of which has its characteristics for evading specific security controls. They also offer cybercriminals options based on different types of targets and different attack vectors.
Why PhaaS Is So Dangerous
The Phishing-as-a-Service threat is greater than the typical phishing threat in several respects. First, the commercial character of such services renders attacks more sophisticated and harder to detect. Second, the subscription-based model ensures constant updates and improvement of attack methods.
PhaaS platforms also include full support systems. Some include customer support, tutorials, and even success guarantees. Such a professional system makes cybercrime more convenient and dependable for the criminal. Additionally, the economies of scale the PhaaS providers have enabled them to invest in advanced evasion techniques that lone attackers cannot.
The worldwide extent of PhaaS activities makes them even more potent. Recent activities have struck 169 targets in 88 countries, showing the globalized extent of the attacks. Moreover, the employment of various communication channels, such as iMessage and RCS smishing, shows how PhaaS vendors evolve to accommodate various platforms.
Comprehensive Protection Strategies Against PhaaS
Multi-Layered Email Security
Having the latest email security technology is the first line of defense against PhaaS attacks. Advanced email security tools take advantage of the strength of artificial intelligence and machine learning to spot suspicious patterns and behavior. Moreover, these tools can detect newly registered domains and suspicious sender reputations most frequently linked to PhaaS campaigns.
Organizations must implement solutions that involve:
- Real-time URL scanning and sandboxing
- In-depth threat intelligence integration
- Behavioral monitoring of email trends
- Automatic quarantine of suspected messages
DNS Filtering and Web Protection
DNS filtering provides another critical countermeasure against Phishing-as-a-Service. By preventing users from accessing known malicious domains and newly registered suspicious domains, DNS filtering can prevent users from visiting phishing websites even when they click on malicious links.
Successful DNS protection must involve:
- Real-time domain reputation checking
- Blocking of newly registered domains for a cooling-off period
- Integration with threat intelligence feeds
- Extensive logging for incident response
Enhanced Authentication Processes
Whereas PhaaS platforms increasingly focus on multi-factor authentication, having strong authentication is still a necessity. Organizations, however, need more than rudimentary MFA to safeguard against advanced PhaaS attacks.
Recommended authentication methods are
- Hardware-based authentication tokens
- Biometric authentication, where possible
- Risk-based authentication that considers context
- Periodic review and rotation of authentication credentials
How ORASEC Defends Against PhaaS Attacks
ORASEC offers end-to-end cybersecurity solutions that are specifically built to counter Phishing-as-a-Service-type threats. Their solution features advanced threat detection and response capabilities that specifically target the challenges posed by PhaaS attacks.
ORASEC protection encompasses:
- Real-time threat intelligence that detects new PhaaS campaigns emerging
- Safer email with artificial intelligence-driven analysis
- In-depth user behavior analytics
- Rapid threat containment emergency response services
- Regular security audits to find vulnerabilities
Further, ORASEC’s cybersecurity specialists monitor the threat environment constantly to ensure their clients are protected against the latest PhaaS threats. Their threat hunting services proactively identify potential compromises before they happen and prevent them from causing damage.
Conclusion
Phishing-as-a-Service (PhaaS) is a new and advanced form of cybercrime that companies must not overlook. The ease of use and sophistication of these tools have made advanced cyber attacks accessible to low-level criminals with little technical expertise. Nevertheless, through the adoption of robust security controls, high alertness, and collaboration with seasoned cybersecurity vendors such as ORASEC, companies can adequately defend themselves against these emerging threats.
The key to success lies in adopting a proactive, multi-faceted cybersecurity approach. On top of that, continuous learning, regular security audits, and diligence in observing new threats are essential components of a successful defense system. As PhaaS evolves, organizations must be adaptable and ready to deploy new defensive solutions.
Act now by evaluating your organization’s current security stance and adopting the defensive measures described in this article. Think about collaborating with ORASEC to maintain your defenses at optimal levels against the constantly changing landscape of phishing-as-a-service attacks.