What is Host-based Intrusion Detection System?
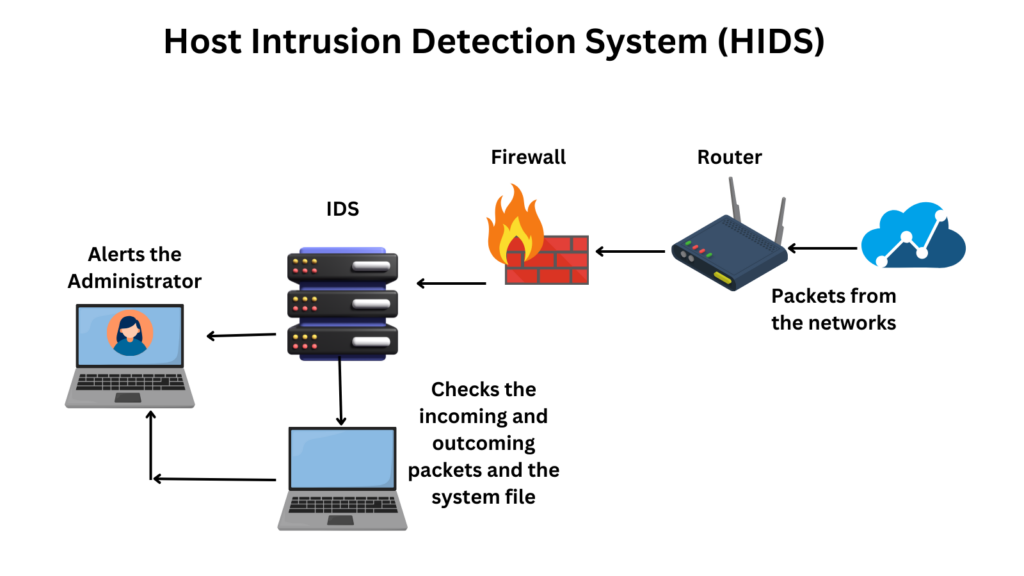
A Host-based Intrusion Detection System (HIDS) is a specialized cybersecurity tool that protects individual computers and servers by monitoring activity on the host itself. Instead of scanning all network traffic, a HIDS focuses on internal data such as system logs, file changes, and running processes to spot unusual behavior. By analyzing events on each host, HIDS can detect anomalies—like a sudden spike in failed logins or modified system files—which may indicate an attack. This deep, host-level monitoring provides an extra layer of security that complements network-based defenses.
HIDS tools typically install an agent or sensor on each endpoint (a host) to collect data, or they gather logs remotely. The system then uses an analytics engine to sift through this data, comparing it to known safe patterns and baselines. When a HIDS identifies a suspicious pattern, it generates alerts or reports so security teams can act quickly. For example, HIDS can detect when a server’s configuration files change unexpectedly or when an application suddenly accesses sensitive data it shouldn’t. In short, a HIDS is a vigilant guard on each host, flagging threats that might slip past network filters.
How HIDS Works
A HIDS functions by continuously gathering and analyzing data from the host’s own sources. It often includes log analysis (examining authentication logs, application logs, etc.), file integrity checking (monitoring critical files for changes), and sometimes network traffic that touches that host. For example, the HIDS might track login attempts, system calls, and firewall logs on a server. Using both signature-based rules (matching known attack patterns) and anomaly-based detection (spotting deviations from normal behavior), it can spot both known malware and novel threats.
When abnormal activity is found, the HIDS can alert the team immediately. Some systems even integrate with response tools to automatically block an attacker (for instance, adding a firewall rule). In addition to real-time alerts, HIDS usually provide detailed reports and dashboards that summarize host security over time. These reports help admins see trends like how often certain servers are targeted and how many anomalies occurred in a month. By correlating information from multiple data sources, HIDS gives a clear picture of security incidents at the host level
Key Components and Features
A complete HIDS solution generally includes:
- Agents/Sensors: Software on each host (agent) or network connectors (agentless) that collect log data.
- Central Storage: Aggregated log and event data stored in a central system for analysis and historical reference.
- Analytics Engine: The core engine that analyzes the data, looking for patterns or anomalies indicating threats.
- Alerting and Reporting: Tools that notify admins of incidents and generate security reports for compliance and auditing.
Additional HIDS features often include file integrity monitoring (verifying critical files haven’t been tampered with) and rootkit detection. Many HIDS also allow custom rule creation, so IT teams can tailor detection to their environment. Because they run on the host, these systems can see application behavior that a network IDS might miss – for instance, a malicious process that starts on a server without obvious network traffic.
HIDS vs. NIDS (Host vs. Network IDS)
HIDS are often compared with Network-based Intrusion Detection Systems (NIDS). The key difference is where they monitor traffic:
- HIDS: Installed on individual hosts (servers, PCs, endpoints), so it watches the host’s own logins, files, processes, and sometimes network packets to/from that host.
- NIDS: Monitors all network traffic at strategic points (like network gateways or switches) to detect threats moving through the network, regardless of host.
In practical terms, HIDS provides granular internal visibility: it can detect if someone is tampering with files on a specific server or if malware is running on a workstation. In contrast, NIDS provides broad network visibility: it detects malicious traffic patterns, scans, or exploits crossing the network boundary.
Both have advantages. For example, an HIDS can spot internal threats like a compromised insider or a malicious process after the initial network intrusion. Meanwhile, a NIDS can catch attacks targeting multiple hosts at once. Often, organizations deploy both HIDS on critical servers and endpoints and NIDS on the network for a layered defense.
Benefits and Importance of HIDS
Deploying a host-based IDS brings several key benefits for cybersecurity:
- Early Threat Detection: By monitoring logs and system state in real-time, HIDS can alert on suspicious activity quickly.
- Granular Visibility: HIDS provides deep insight into each host’s behavior. They can identify insider threats or malware that don’t generate obvious network traffic.
- Automated Response: Some HIDS can auto-remediate. For instance, if a host detects its file system is under attack, it could auto-adjust firewall settings.
- Compliance and Forensics: HIDS keeps detailed logs of host activity (login history, file changes, etc.), which helps meet security compliance and aids incident response.
- Low Network Impact: Because HIDS processes data on each host, they typically use less network bandwidth than heavy network monitoring.
In short, HIDS are an essential layer of defense for servers, endpoints, and any critical system
Open-Source HIDS Tools and Examples
There are several popular host-based IDS tools—both open-source and commercial. Here are a few examples:
- OSSEC: A widely used open-source HIDS. It supports log analysis, file integrity checking, rootkit detection, and alerts on both Linux and Windows systems.
- Wazuh: A fork of OSSEC that adds scalability and integration (e.g., with ELK/Elastic Stack). Wazuh offers anomaly detection, registry monitoring, and container monitoring.
- Samhain: An open-source HIDS focusing on file integrity and log monitoring, with encrypted communication and stealth capabilities to hide from attackers.
- Tripwire (Open-Source Edition): Runs on Linux for file integrity monitoring. It can detect tampered system files, though it’s mainly scan-based and not always real-time.
- Security Onion: A free Linux distribution that includes HIDS and NIDS tools for enterprise monitoring.
Limitations and Best Practices
While powerful, HIDS have some limitations. For one, they must be installed on every host you want to protect. This can be resource-intensive: HIDS agents consume CPU, memory and disk for logging. If misconfigured, they can slow down servers. Additionally, a HIDS only sees the host it’s on. It cannot by itself protect hosts it isn’t installed on, nor see other parts of the network. Therefore, HIDS should be part of a defense-in-depth strategy along with other tools (like NIDS, firewalls, and application scanners).
Best Practices:
- Monitor all critical hosts, including servers, workstations, and appliances.
- Correlate HIDS data with other security logs to reduce false positives.
- Tune alerts to prevent overload and prioritize critical issues.
- Keep detection rules updated.
- Use agentless options in large environments if resources are a concern.
Conclusion
A Host-based Intrusion Detection System (HIDS) is a vital component of any layered cybersecurity strategy. By watching the internals of each host, HIDS tools catch threats that network-only defenses might miss. In this post, we explained what HIDS is, how it works, and why it’s important—including key differences from NIDS, its benefits, and examples of popular tools. For IT professionals and admins, implementing HIDS means gaining deeper insight into endpoint security and being able to stop attacks on hosts quickly. Organizations seeking comprehensive security assessments can benefit from partnering with expert firms like OraSec.
Organizations can greatly improve their threat detection capabilities by deploying a robust HIDS (or HIPS) and combining it with network monitoring and other defenses. Stay proactive: consider adding an HIDS to your security toolkit today to monitor and protect your servers and devices from insider threats, malware, and other breaches.
Frequently Asked Questions
Q1: What is the difference between an HIDS and an HIPS?
An HIDS monitors and alerts on suspicious host activity, while an HIPS goes further by automatically blocking or isolating detected threats.
Q2: Why might I need both HIDS and NIDS in my security strategy?
HIDS protects each server or endpoint, while NIDS monitors the overall network. Together, they provide a defense-in-depth approach.
Q3: Can I use an HIDS for compliance?
Yes. HIDS logs detailed activity that helps demonstrate compliance with standards like PCI-DSS, HIPAA, and ISO 27001.