3 Best Ways to Speed Up Alert Triage for SOC Team – Use Cases
Security Operations Centers (SOCs) are struggling more than ever: handling tens of thousands of security alerts and doing it both promptly and correctly. Alert triage has become SOC teams’ main operational bottleneck that determines the organizational capacity to perform cybersecurity. And modern threat landscapes demand immediate responses that manual processes simply cannot provide.
Security analysts dedicate about 25% of their time to alert triage tasks, while many organizations are based on antiquated manual processes. Besides that, the average SOC deals with about 11,000 alerts every month, and only 22% of these need actual investigation. Therefore, placing effective alert triage for SOC team workflows is crucial to the organizational security posture.
Understanding Current SOC Alert Issues
Security teams encounter several critical challenges that slow down alert triage processes. First, alert fatigue affects analyst productivity significantly, while false positives consume valuable resources. Additionally, manual investigation processes create delays that attackers exploit effectively.
The complexity of modern threat vectors requires sophisticated analysis capabilities. In addition, organizations must balance speed with accuracy to avoid missing critical threats. Therefore, implementing automated solutions becomes crucial for effective alert triage for SOC team operations.
Method 1: Implement Cloud-Based Sandbox Solutions
Transforming Malware Analysis Efficiency
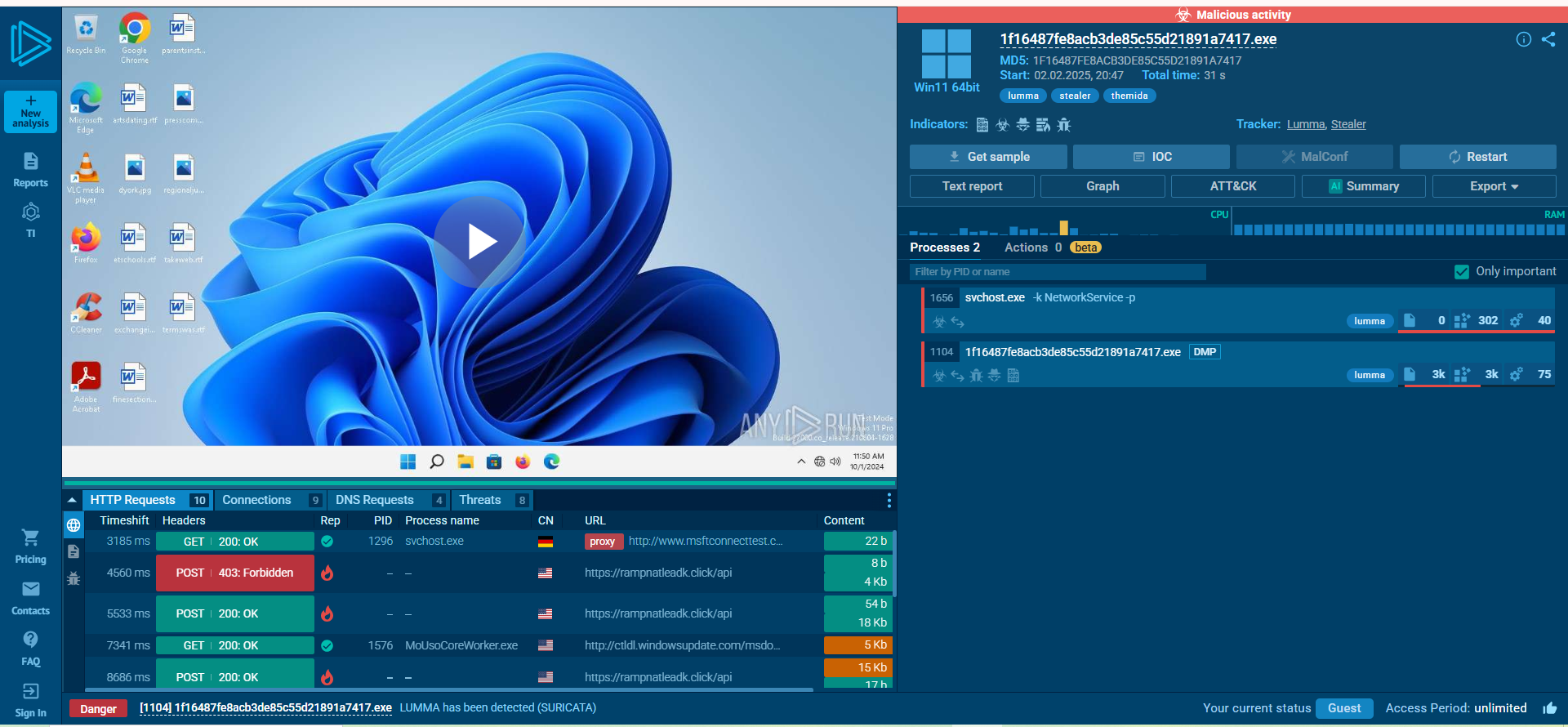
Cloud sandboxing technology changes the face of analyzing questionable files and URLs by SOC teams. Analysts no longer have to configure virtual machines by hand but instead are instantly presented with isolated test environments. Additional solutions offer full threat analysis functionality with no infrastructure overhead.
Modern cloud sandboxes offer several advantages over traditional VM setups. First, they eliminate configuration time, enabling immediate threat analysis. Additionally, they provide scalable resources that handle multiple investigations simultaneously. Moreover, automatic cleanup processes ensure consistent testing environments.
Key Benefits of Cloud Sandbox Implementation
Cloud-based analytical platforms bring real-time value within multiple mechanisms. The SOC team’s alert triage speeds up immensely when analysts can access pre-configured environments within minutes. Also, these solutions apply to diverse operating systems and network configurations with no local resource limitations.
Interactive analytical functionality facilitates observing malware activity in real time. Next, automated extractions of artifacts significantly cut the time spent investigating by hand. Hence, analysts spend more time doing threat assessment than infrastructure management.
Real-World Implementation Examples
Companies using cloud sandbox solutions document staggering increases in efficiency. For example, the time spent analyzing a phishing e-mail decreases from 45 minutes to just 10 minutes. Moreover, identification of malware families takes place within seconds or minutes instead of hours.
Sophisticated tools such as ANY.RUN offers in-depth analysis features with automatic attachment detection and phishing URL identification. Further, these tools detect advanced evasion methodologies automatically. Hence, the SOC team workflows’ alert triage becomes greatly streamlined.
Method 2: Deploy Intelligent Automation Systems
Automating Repetitive Investigation Tasks
Automation minimizes laborious tasks that don’t necessarily involve human expertise. At first, automated processes handle very effectively first-level alert prioritizations and sorting. Further, they perform preliminary enrichment work like IP reputation validation and domain analysis.
Intelligent automation platforms are integrated with available security tools seamlessly. Also, they ensure investigation continuity and cut the analyst workload significantly. Thirdly, automation processes are consistent and eliminate human error variables that distort investigation quality.
Advanced Automation Capabilities
Today’s automation platforms carry out intricate tasks of analysis previously needing human intervention. Alert triage of SOC team operations is made better by automated detection of artifacts, behavioral analysis, and threat correlation. Moreover, these systems produce standardized output of reports, making decision-making processes easier.
Intelligent automation evolves based on organizational workflows and attack patterns. Also, detection accuracy enhances with time through machine learning capabilities. Hence, automation gets better while still investing adequately.
Streamlining Phishing Investigation Workflows
Phishing cases are perfect examples of automation’s revolutionary effect on SOC operations. Automated tools pluck URLs from PDF attachments, scan QR codes, and inspect landing pages without human intervention. They can also detect attempts at credential harvesting and brand impersonation.
Real-time analytical functionality facilitates immediate threat determination and response coordination. Further, automation of documentation ensures complete records of investigations for compliance purposes. As a result, alert triage of the SOC team’s effectiveness is improved significantly.
Method 3: Integrate AI-Powered Decision Support
Enhancing Analyst Capabilities with Artificial Intelligence
Artificial intelligence complements human expertise, not substituting analyst judgment. Initially, AI systems detect imperceptible threat signs that may go undetected by manual analysis. They also give contextual insights that boost decision-making processes considerably.
Machine-driven platforms scan vast data sets and identify threat profiles and anomalous activity. Further, they can generate actionable intel that informs efficient investigation priorities. Further, natural language processing functionality translates complex technical data into actionable insights.
Privacy-Focused AI Implementation
Enterprises need AI offerings that are both data confidential and regulatory compliant. The SOC team implementable alert triages need to keep sensitive data within the confines of the organization. Moreover, processing on-premises reduces third-party data exchange issues.
Sophisticated AI platforms offer real-time threat summaries and behavioral analytics based on absolutely no external dependence. Also, they seamlessly integrate with deployed security infrastructure. Hence, organizations enjoy data control while leveraging AI functionalities.
Practical AI Application Scenarios
AI assistance is not only indispensable but also essential when analysts are up against unknown threat activity or next-gen attack tactics. For instance, AI identifies cryptocurrency mining activities, credential stuffing attempts, and advanced persistent threat activity autonomously. Further, it identifies unrelated events and discovers attack campaigns.
Machine learning programs gradually enhance detection capacities using organizational threat profiles. Also, AI programs evolve when new attack methodologies emerge and do not need manual updates of rules. As such, alert triage enhances SOC team efficiency over time.
Leveraging OraSec’s Expertise for Enhanced Security
While implementing these alert triage improvements, organizations often discover vulnerabilities that require specialized attention. OraSec provides comprehensive penetration testing services that identify security weaknesses before attackers exploit them. Furthermore, their expert-led assessments deliver actionable insights for strengthening organizational defenses.
OraSec’s customized methodology makes penetration testing scalable and adaptable to the special needs and threat profiles of specific organizations. Moreover, their detailed report includes remediation priority-based recommendations for closing vulnerabilities. Hence, the organizations can remediate security gaps pre-emptively and streamline alert triage for effective SOC team functioning.
Implementation Best Practices and Considerations
Strategic Planning for Technology Integration
Proper alert triage to optimize SOC teams involves careful planning and staged execution. Initially, organizations ought to review workflows currently being used and spot particular bottlenecks. They are also required to ensure new technologies blend well with the deployed security infrastructure.
Then, change management is essential for analyst adoption and work streamlining. Also, training programs make sure teams take advantage of new technology features. And phased rollouts ensure minimal disruption of work while facilitating constant innovation.
Measuring Success and ROI
Organizations must establish metrics for measuring alert triage for SOC team improvement initiatives. Key performance indicators include mean time to triage, false positive rates, and analyst productivity metrics. In addition, cost-benefit analysis demonstrates return on investment for security technology investments.
Regular assessment ensures optimization strategies remain effective as threat landscapes evolve. Furthermore, continuous monitoring identifies additional improvement opportunities. Therefore, organizations maintain competitive security postures through ongoing optimization efforts.
Conclusion
Effective alert triage of SOC teamwork requires innovative approaches integrating cloud technologies, intelligent automation, and AI-based analysis. Further, these implementations considerably reduce investigation time and boost the detection accuracy of those recognized threats.
Companies implementing these three strategies have remarkable upward trajectories of analyst productivity, incident response times, and overall security posture. And fewer false positives leave more time for teams to handle real problems that are urgent.
The information security environment requires persistent innovation and dynamism. Hence, SOC staff have to adopt cutting-edge technologies, boosting human capabilities and not substituting the expertise of analysts. Besides that, strategic deployment secures maximum return on information security technology investment.
Ready to revamp SOC operations? Call OraSec now and find out what it takes to integrate effective penetration testing with your improved alert triage functionality and fortify your overall security posture.