Top 10 Best Supply Chain Intelligence Security Companies in 2025
The digital landscape is changing quickly. Companies now face rising threats from software vulnerabilities, data breaches, and complex cyber supply chain attacks. As organizations use more open-source components and third-party code, securing these networks is essential. This growing risk underscores the need for advanced supply chain intelligence security.
To protect your business, you need the right platform. By 2025, organizations will require reliable tools that provide visibility, compliance, and security across their software supply chains. This guide presents the Best Supply Chain Security Companies of the year. We analyze each tool, highlighting unique features, reasons to buy, and insights into pros and cons.
Why Is Supply Chain Intelligence Security Crucial in 2025?
The development environment is becoming more complex. Thus, supply chain attacks are an unavoidable risk. From dependency hijacking to vulnerable packages, businesses need tools that can monitor, prevent, and mitigate risks instantly.
The companies on our 2025 list offer cutting-edge threat intelligence, continuous monitoring, and compliance management. Choosing the right software can determine whether a business continues or suffers a devastating cyberattack. Also, these platforms set industry standards with features like real-time vulnerability detection and AI-driven risk analytics.
Comparison Table: Top 10 Best Supply Chain Intelligence Security Companies 2025
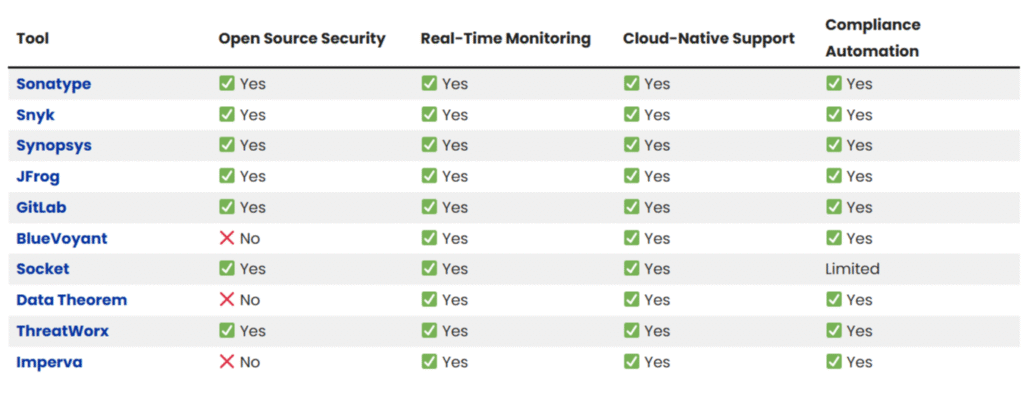
Top 10 Best Supply Chain Security Companies
Sonatype: The AI-Driven Leader
Sonatype is a leading company protecting software supply chains with its Nexus platform. It automates open-source governance, compliance, and security.
Specifications
Comprehensive Software Composition Analysis (SCA) and continuous monitoring. It integrates seamlessly with CI/CD and developer tools.
Features:
Automated vulnerability scanning, customized policy enforcement, real-time supply chain intelligence, and malicious code detection.
Reason to Buy:
Sonatype offers unmatched AI-powered intelligence and enterprise-grade governance. Its broad ecosystem support ensures smooth integration for enterprises practicing DevSecOps at scale.
Pros:
Advanced AI-driven supply chain monitoring, deep open-source governance, and an extensive vulnerability database.
Cons:
Higher cost for small businesses; steep learning curve for beginners.
Best For:
Enterprises need scalable, AI-driven supply chain security across development and production.
Snyk: The Developer-First Choice
Snyk changed how developers handle security by fixing vulnerabilities early in the development lifecycle. It offers automated detection across open-source dependencies and containers.
Specifications:
Multi-layered security across packages, containers, and infrastructure. It uses a scalable SaaS-based model.
Features:
AI-powered scanning, deep security testing for dependencies, license compliance verification, and automated fixes.
Reason to Buy
Organizations benefit from its strong developer-first design. It covers every stage of the development cycle, ensuring complete Cyber Supply Chain Protection for cloud-native enterprises.
Pros:
Easy-to-use, developer-centric design; wide integration ecosystem; intelligent vulnerability prioritization.
Cons:
Limited offline support; pricing can be challenging for startups.
Best For:
Developer teams seek security built into their coding and CI/CD pipelines.
Synopsys: Compliance and Scale
Synopsys is a global leader in software security. Its Black Duck solution is widely used by enterprises to manage risks from open-source software.
Specifications:
Scalable Software Composition Analysis (SCA) for vulnerability and license compliance scanning. It integrates into CI/CD pipelines.
Features:
Deep scanning of dependencies, advanced risk management, and real-time intelligence on malicious components.
Reason to Buy:
Synopsys is a trusted vendor in risk- and compliance-heavy industries. Its governance gives companies granular control over supply chain security.
Pros:
Strong compliance capabilities; detailed risk insights with enterprise scalability; Extensive Vulnerability Management.
Cons:
Complex features may require extensive training; they are more suited for enterprises.
Best For:
Enterprises with strong compliance requirements and large-scale operations.
JFrog: Binary and Artifact Assurance
JFrog focuses on securing the entire DevOps lifecycle with its Artifactory and Xray solutions. It ensures complete integrity across software artifacts.
Specifications:
JFrog Xray integrates with Artifactory, providing end-to-end visibility across binaries and open-source components.
Features:
Automated binary scanning, integrated policy enforcement, and supply chain vulnerability alerts.
Reason to Buy:
JFrog excels in protecting organizations at the binary level. In addition, it delivers “shift-left” security while keeping development pipelines agile.
Pros:
Best-in-class binary scanning, highly integrative ecosystem, and real-time monitoring of vulnerabilities.
Cons:
Complex for non-technical teams; premium cost for complete package.
Best For:
DevOps-driven organizations need deep artifact-level assurance.
GitLab: Unified DevSecOps Platform
GitLab provides an integrated DevSecOps platform. It ensures every commit, dependency, and release meets the highest security standards.
Specifications:
Built-in continuous integration system with SCA, SAST, and Vulnerability Management.
Features:
Built-in application security testing, compliance automation, and developer workflow integration.
Reason to Buy:
GitLab significantly reduces complexity by combining DevOps workflows and security in a single platform. For instance, unified solutions offer superior efficiency.
Pros:
All-in-one DevSecOps platform; seamless CI/CD and SCM security integration; enhanced threat visibility.
Cons:
Feature-richness may overwhelm beginners; the Ultimate tier is costly for small teams.
Best For:
Teams want a unified platform for code management and supply chain security in one interface.
BlueVoyant: Managed Third-Party Risk
BlueVoyant specializes in managed supply chain risk and intelligence. It manages Third-Party Risk at scale.
Specifications:
A managed platform with 24/7 monitoring of supply chain vulnerabilities. It uses predictive modeling.
Features:
Detailed monitoring dashboards, third-party security performance scoring, and remediation guidance.
Reason to Buy:
Companies with complex vendor ecosystems gain peace of mind through ongoing monitoring and support from BlueVoyant’s security experts.
Pros:
Managed service support reduces workload; Strong focus on vendor risk; Excellent for compliance-heavy industries.
Cons:
Less developer-focused; requires external engagement with service teams.
Best For:
Enterprises with complex third-party ecosystems need managed risk protection.
Socket: Open-Source Malware Defense
Socket focuses on protecting open-source security ecosystems against supply chain attacks. It detects hidden malware and suspicious network activity in code libraries.
Specifications:
Open-source package monitoring and behavioral analysis. It integrates with popular package managers like npm and Yarn.
Features:
Dependency malware detection, unusual permission request analysis, and real-time alerts.
Reason to Buy:
Socket offers unmatched protection against supply chain malware by focusing on the behavioral analysis of packages, going beyond standard CVEs.
Pros:
Open-source security malware focus, innovative behavioral analysis, and lightweight developer integration.
Cons:
Still growing its enterprise adoption; Limited compliance automation.
Best For:
Developer teams heavily reliant on open-source tools who need granular malware protection.
Data Theorem: API and Cloud Focus
Data Theorem secures APIs, applications, and cloud systems. It delivers visibility into vulnerabilities across the software supply chain, especially for microservices.
Specifications:
Combines vulnerability scanning, automated compliance testing, and DevOps integration. It supports web, API, and mobile apps.
Features:
API threat detection, app vulnerability scanning, compliance automation, and DevOps pipeline integration.
Reason to Buy:
Enterprises relying heavily on APIs or mobile apps gain strong supply chain protection with Data Theorem’s tailored coverage.
Pros:
Excellent API and mobile security; Automated vulnerability management; Robust DevOps integration.
Cons:
Less focus on traditional open-source risks; Advanced features may require expert use.
Best For:
Enterprises with API-driven architectures and mobile-first strategies.
ThreatWorx: Predictive Intelligence
ThreatWorx stands out for its strong emphasis on intelligence and proactive threat modeling. It merges SCA with global threat intelligence feeds.
Specifications:
Real-time Vulnerability Management, policy enforcement, and integration with CI/CD pipelines. It uses AI modules for risk prioritization.
Features:
Continuous monitoring, real-time dashboards, AI-based risk prediction, and compliance verification.
Reason to Buy:
For enterprises seeking to go beyond reactive scanning, ThreatWorx delivers sophisticated, intelligence-led supply chain security.
Pros:
Predictive AI-driven risk analytics; Continuous DevOps-friendly coverage; Global threat feed integration.
Cons:
Smaller market share compared to market leaders; Limited details on open-source remediation.
Best For:
Organizations that require predictive risk assessment and integrated global threat intelligence.
Imperva: Web Application Defense
Specifications:
Application security suite including Web Application Firewall (WAF) and API security gateway. Offers high scalability and cloud-native support.
Features:
Application and API security, DDoS protection, WAF, Real-time risk monitoring, and bot attack mitigation.
Reason to Buy
Imperva provides strong defense against threats that target the application components of the supply chain, such as malicious bots and web exploits.
Pros:
Strong web application protection; High scalability, Comprehensive security suite.
Cons:
Not solely focused on Software Composition Analysis (SCA); Can be costly.
Best For:
Large enterprises need robust web and API security as a crucial part of their overall supply chain defense.
Beyond the Tools: The Role of Penetration Testing
While these advanced platforms offer excellent continuous monitoring and vulnerability scanning, a complete Cyber Supply Chain Protection strategy requires independent verification. This is where expert security services are vital.
For example, a security partner like OraSec helps by providing comprehensive penetration testing services. They specialize in Web, Mobile, API, Network, and Internal Infrastructure Pentesting. This proactive service uncovers hidden weaknesses before hackers strike. By simulating real-world attacks, OraSec allows you to fortify your defenses and ensure your internal and external systems—which form your operational supply chain—are resilient.
Conclusion
Securing the digital supply chain is non-negotiable in 2025. Choosing one of these Best Supply Chain Security Companies is a necessary first step toward achieving resilience. We have discussed solutions ranging from developer-focused tools like Snyk to managed services like BlueVoyant and highly integrated platforms like GitLab. Ultimately, the right choice depends on your organization’s size, development maturity, and specific compliance needs.
Call to Action: Don’t wait for a breach to happen. Evaluate these top 10 companies today, and begin implementing robust Cyber Supply Chain Protection to safeguard your business’s future.
