What is Cross-Site Request Forgery?
Cross-Site Request Forgery (CSRF) is one of the deadliest and most underrated web security vulnerabilities, and it continues to haunt current apps. Moreover, learning this attack methodology is extremely necessary for everyone engaged with web development or information security. This detailed primer will delve into all that you need to learn regarding CSRF attacks and protection.
What Does Cross-Site Request Forgery Do?
Cross-Site Request Forgery, also abbreviated as CSRF or XSRF, is a security attack in which unauthorized instructions are fed from a trusted user to a web app. This attack takes advantage of a web app’s confidence that a browser belongs to an authenticated user. In addition, hackers may dupe users into undertaking undesirable activities without their consciousness or agreement.
The attack takes advantage of the default inclusion of auth credentials (for example, session cookies) into the HTTP requests. As a result, when a user accesses a malicious website from a logged-in state in a legitimate app, the attacker forges requests that appear to originate from the logged-in user.
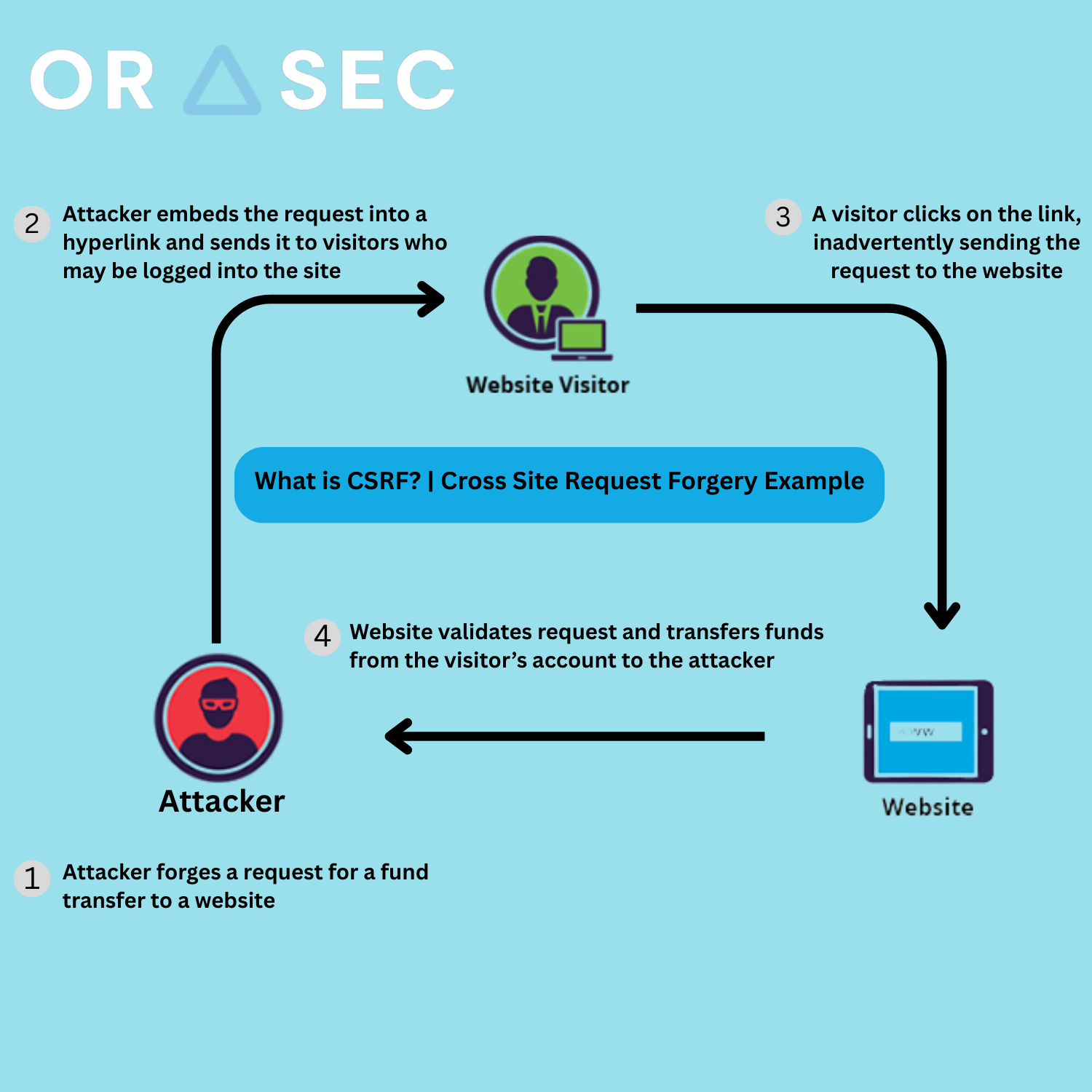
How Cross-Site Request Forgery Attacks Work
The Attack Mechanism
First, the victim must be authenticated on the target website. Second, the attacker creates a malicious webpage containing hidden forms or JavaScript code. Third, when the victim visits the malicious page, it automatically triggers a request to the target site. Finally, the target site processes the request as if it came from the legitimate user.
Real-World CSRF Attack Scenarios
Banking Transfer Example:
The attacker would construct a form that would submit itself when the webpage is visited by an online customer. In addition, the bank server would honor this form submission because it comes with valid session cookies.
Social Media Manipulation: Attackers might force users to post unwanted content, change privacy settings, or send friend requests without the user’s knowledge. Additionally, these actions could damage the victim’s reputation or compromise their privacy.
Email Account Takeover: CSRF attacks can modify email forwarding rules, change passwords, or add unauthorized email addresses to recovery options. Moreover, this could lead to complete account compromise.
Types of Cross-Site Request Forgery Attacks
GET-Based CSRF Attacks
These attacks use simple HTTP GET requests embedded in images, links, or JavaScript. Additionally, they’re easier to execute but limited in scope since GET requests should only retrieve data.
html
<img src="https://bank.com/transfer?amount=1000&to=attacker" width="0" height="0" />POST-Based CSRF Attacks
The attacks are more advanced and involve POST requests via hidden forms that auto-submit upon page load. Additionally, the attacks are capable of executing more advanced actions, such as modifying data.
JSON-Based CSRF Attacks
JSON API applications in modern applications are not yet immune from attacks if proper CSRF protection is not followed. Additionally, malicious actors can utilize JavaScript to send JSON payloads to vulnerable points.
Impact and Consequences of CSRF Attacks
The aftermath of successful Cross-Site Request Forgery attacks can be devastating:
Financial Damage: Unapproved transactions, fund transfers, or buys can lead to immediate financial harm. Moreover, companies can have liability issues and regulatory fines.
Data Exposure: CSRF attacks can change user profiles, update email addresses, or update security settings. Moreover, this can result in total account takeovers and data leaks.
Reputation Harm: When users post offensive content unintentionally or take unwanted actions, it can heavily harm their professional or personal reputation.
Business Disruption: Massive CSRF attacks have the potential to overload systems and cause disruption to usual business activities. Additionally, the cleanup and investigation process would be expensive and time-consuming.
Common CSRF Vulnerabilities in Web Applications
Lack of Anti-CSRF Tokens
Most applications lack adequate token-based protection schemes. Some developers also depend on referrer headers, which are vulnerable.
Inadequate State Management
Applications without the correct validation of request sources are highly susceptible. Also, weak session management will amplify CSRF vulnerabilities.
CORS Misconfigurations
Misconfigured Cross-Origin Resource Sharing policies allow for CSRF attacks. Also, overly liberal CORS settings expose applications to multiple vectors of attack.
Prevention Strategies and Best Practices
Anti-CSRF Tokens (Synchronizer Tokens)
The best protection against Cross-Site Request Forgery is using anti-CSRF tokens. In addition, the tokens must be unique, unpredictable, and session-based for the user.
Implementation Steps:
- Create a unique token for every user session
- Embed the token in all forms and AJAX requests
- Verify the token on the server prior to processing the requests
- Deny requests lacking or containing invalid tokens
SameSite Cookie Attribute
Modern browsers support the SameSite attribute for cookies, which prevents their inclusion in cross-site requests. Furthermore, this provides an additional layer of protection against CSRF attacks.
javascript
Set-Cookie: sessionid=abc123; SameSite=Strict; Secure; HttpOnlyDouble Submit Cookies
This method involves storing a random value within a cookie and an ordinary request parameter. Further, the server checks that both values are equal before acting on the request.
Custom Headers Verification
Addition of custom headers to AJAX requests may help avoid CSRF attacks because browsers do not support custom headers for cross-domain requests without CORS enablement. Further, this method is suitable for API endpoints.
Referrer Header Validation
Although not infallible, examining the Referer header can offer an added measure of security. In addition, blocking requests from unknown origins can ward off some attacks.
Testing for CSRF Vulnerabilities
Manual Testing Methods
Burp Suite CSRF PoC Generator: This utility can automatically generate proof-of-concept pages for possible CSRF vulnerabilities. In addition, it assists security experts in illustrating the effects of found flaws.
OWASP ZAP: The Zed Attack Proxy has CSRF detection and the ability to scan applications for vulnerable endpoints. Additionally, it reports on discovered issues in detail.
Custom Test Scripts: It is possible for developers to have them create basic HTML pages and test if their applications validate request origins correctly. Additionally, automated testing may be embedded into CI/CD pipelines.
Automated Vulnerability Assessment
Professional security services such as OraSec offer extensive penetration testing that involves CSRF vulnerability testing. Secondly, their skilled pentesters are capable of discovering hidden vulnerabilities that automated tools cannot detect. Thirdly, OraSec’s in-depth reports contain recommendations for remediation of CSRF vulnerabilities and other vulnerabilities.
Advanced CSRF Protection Techniques
Token-Based Authentication with JWT
JSON Web Tokens can also offer further protection when used correctly. Secondly, token storage within HTTP-only cookies and token validation per request further boost security.
Content Security Policy (CSP)
Enforcing strict CSP headers may disable the execution of malicious scripts that could enable CSRF attacks. Secondly, CSP can disallow unauthorized external resources.
Multi-Factor Authentication
For critical actions, the addition of extra authentication steps can stop unauthorized activity even when CSRF attacks take place. Also, this introduces a human verification factor to the process.
CSRF vs. Other Web Attacks
CSRF vs. Cross-Site Scripting (XSS)
Whereas XSS takes advantage of trust between applications and users, Cross-Site Request Forgery takes advantage of trust between users and applications. Also, XSS attacks involve injecting malicious scripts, while CSRF attacks involve forging requests.
CSRF vs. Session Hijacking
Session hijacking is the act of stealing session identifiers, while CSRF attacks utilize valid current sessions to issue unauthorized requests. Also, CSRF does not involve the act of stealing credentials.
Industry Standards and Compliance
OWASP Top 10
Cross-Site Request Forgery was historically included in the OWASP Top 10 list of web application security risks. Additionally, it remains a significant concern in modern web security frameworks.
PCI DSS Requirements
Payment Card Industry compliance requires protection against CSRF attacks for applications handling credit card data. Furthermore, regular security assessments must include CSRF testing.
GDPR and Data Protection
CSRF vulnerabilities can lead to unauthorized data access or modification, potentially violating data protection regulations. Moreover, organizations must implement appropriate technical measures to prevent such attacks.
Conclusion
Cross-Site Request Forgery is still a serious security flaw that needs proactive defensive actions. Moreover, insight into attack vectors and deploying adequate protection measures is mandatory for ensuring secure web applications. Even more, periodic security audits and being well-informed with current protection strategies will ensure that your applications remain protected.
Don’t wait until a security breach lays bare your weaknesses. Furthermore, professional security services such as OraSec can assist in identifying and resolving CSRF vulnerabilities prior to attackers taking advantage of them. Additionally, their full-range penetration testing services offer the expertise necessary to safeguard your business against emerging cyber threats.