Digital Lock Needs an Upgrade: Is Your Password a Welcome Mat for Hackers?
Your digital lock is the first defense against cybercriminals, yet most people treat their passwords like welcome mats for hackers. In today’s interconnected world, weak authentication methods create vulnerabilities that can compromise your entire digital life. Furthermore, understanding why your digital lock needs an upgrade is crucial for maintaining online security and protecting sensitive information.
The State of Password Security: A Digital Lock Under Siege
Modern cybersecurity threats have changed significantly today. Additionally, old password practices do not adequately address advanced threats. Furthermore, users persistently utilize weak passwords that are essentially open invitations to attackers.
Today’s cybersecurity statistics reveal alarming patterns. First, over 80% of data breaches are due to poor or stolen passwords. Second, hackers have automatic programs capable of cracking weak passwords instantly. Therefore, it becomes imperative to improve your digital lock tactic as part of overall security.
Why Passwords Fail As Electronic Locks
Legacy password security controls have several serious problems. In addition, the vulnerabilities provide opportunities for hackers to steal user accounts and confidential data.
Common Password Vulnerabilities:
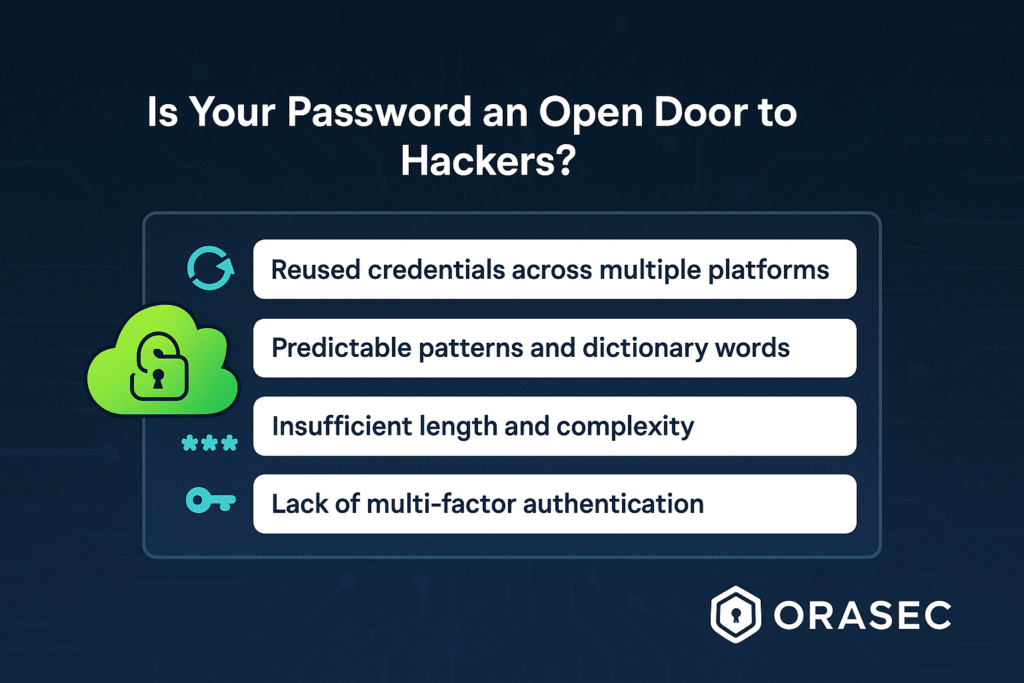
Furthermore, many users underestimate the importance of password hygiene. Consequently, their digital lock remains vulnerable to various attack vectors.
Advanced Threats Targeting Your Digital Lock
Credential Stuffing and Brute Force Attacks
Cybercriminals use advanced methods to crack your online lock. Furthermore, automated tools are used to try millions of password combinations in minutes. Additionally, artificial intelligence now fuels advanced password-cracking software.
OraSec’s penetration testing offerings have found the same vulnerabilities in 400+ organizations worldwide. Their checks by seasoned experts find that insecure passwords leave the door open for hackers. Furthermore, their comprehensive reports provide actionable information to strengthen online security measures.
Social Engineering and Phishing Attacks
In addition to technical attacks, hackers also take advantage of human psychology. In addition, phishing emails trick users into revealing login credentials voluntarily. Therefore, even strong passwords are compromised through social engineering tactics.
Securing Your Digital Lock: Contemporary Security Measures
Multi-Factor Authentication:
More Than the Simple Digital Lock
Multi-factor authentication (MFA) turns your ordinary digital lock into a sophisticated security system. In addition, MFA requires a number of verification processes before access is granted. Besides, the process strongly dissuades successful attacks.
MFA Implementation Advantages:
1. Reduces account takeover risk by 99.9%
2. Provides additional security layers
3. Protects against credential theft
4. Supports remote access securely
Password Managers: Your Digital Lock Guardian
Password managers are the advanced digital lock-and-key mechanisms for the modern user. Further, they generate unique and strong passwords for every account. Additionally, they eliminate the need to memorize lots of credentials.
Key Password Manager Features:
- Automated password creation
- Safe credential storage
- Cross-platform synchronization
- Breach notice monitoring
The Function of Biometric Authentication
Biometric authentication is the future of digital lock technology. Additionally, fingerprints, face recognition, and voice prints offer singular identification techniques. Thus, these biological signs generate virtually uncopyable security credentials.
Deploying Biometric Security
First, turn on biometric authentication on every supported platform. Second, use biometrics and customary passwords together for greater security. Third, update biometric templates routinely for security efficacy.
Enterprise-Level Digital Lock Solutions
Zero Trust Architecture
Organizations must adopt zero-trust thinking to achieve overall security. Also, the approach treats every request for access as potentially malicious. Also, continuous verification offers ongoing protection against evolving threats.
Zero Trust Deployment:
- Check all devices and users
- Restrict access to resources required
- Monitor all network traffic
- Implement ongoing authentication
Future-Proofing Your Digital Lock
Emerging Technologies
Quantum computing offers both opportunities and challenges for digital security as well. In addition, the need for secure communication will eventually necessitate post-quantum cryptography. Therefore, staying current with the newest technology prepares for future security needs.
Continuous Security Monitoring
Proactive monitoring can detect threats before they cause damage. Additionally, automated security devices can identify unusual patterns of activity. Furthermore, 24/7 monitoring offers 24-hour security from constantly evolving threats.
Conclusion
Your online lock requires urgent attention and strategic adjustments. Additionally, embracing contemporary security procedures guards against existing and impending dangers. Thus, acting now averts expensive security breaches and preserves digital secrecy. Need to update your electronic lock? Call OraSec today to arrange for a thorough security audit. Their experienced team will determine vulnerabilities and make helpful suggestions for securing your digital security.
