Enterprise Mobility Management: Essential Components for Modern Business Security
In today’s digital landscape, Enterprise Mobility Management has become a cornerstone of organizational security strategy. As businesses increasingly rely on mobile devices and remote work capabilities, furthermore, the need for comprehensive mobile device management has never been more critical. Enterprise Mobility Management provides organizations with the tools and frameworks necessary to secure, monitor, and manage mobile devices while maintaining productivity and user experience.
What is Enterprise Mobility Management?
Enterprise Mobility Management represents a comprehensive approach to securing and managing mobile devices, applications, and data within an organization. Moreover, this technology framework enables IT administrators to maintain control over corporate resources while allowing employees the flexibility to work from various devices and locations. The evolution of EMM solutions has transformed how businesses approach mobile security, making it an indispensable component of modern IT infrastructure.
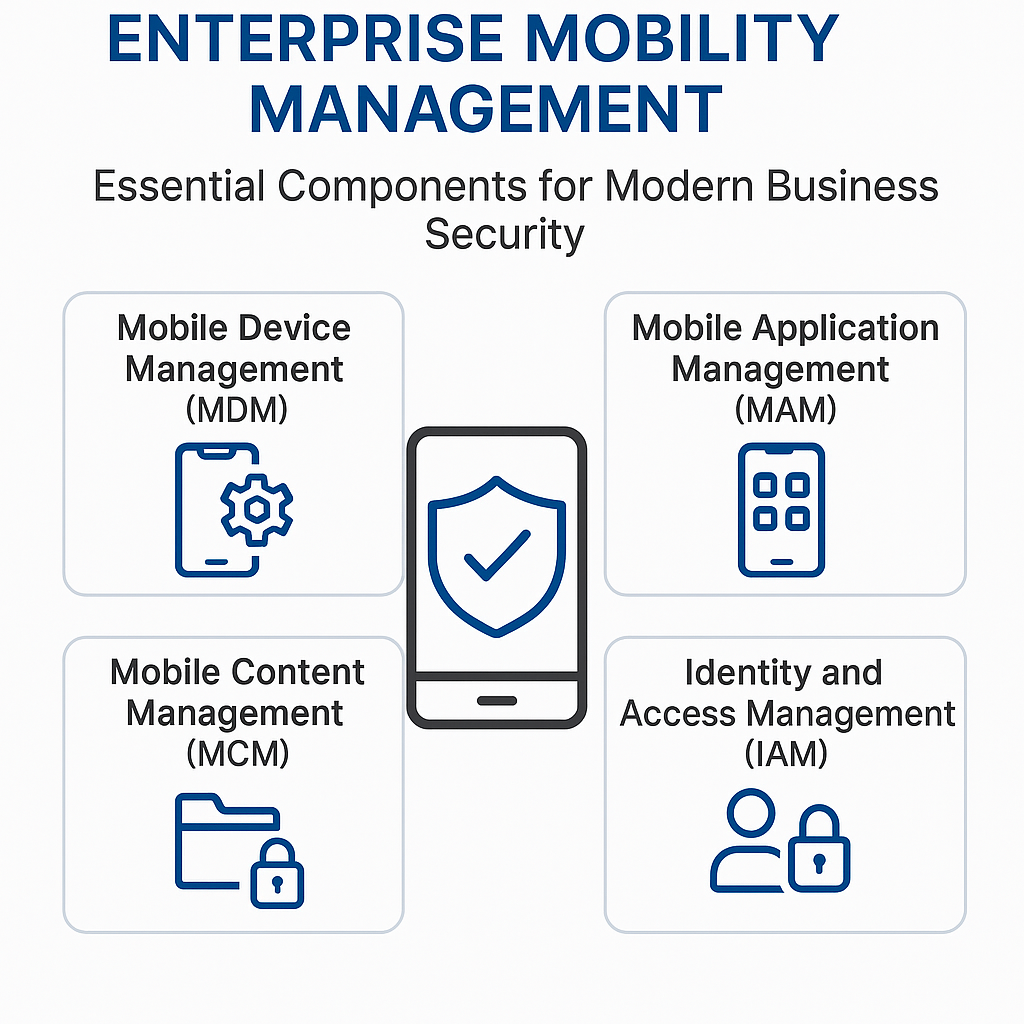
Core Components of Enterprise Mobility Management
Mobile Device Management (MDM)
Mobile Device Management is the cornerstone of any Enterprise Mobility Management solution. MDM solutions also give IT staff centralized management of device configurations, security policies, and compliance tracking. With MDM features, organizations can remotely erase devices, apply password policies, and block unauthorized applications.
Important MDM features are:
- Device enrollment and provisioning
- Remote device monitoring and control
- Security policy enforcement
- Application installation and uninstallation
- Data protection and encryption
Mobile Application Management (MAM)
Mobile Application Management is specifically concerned with controlling and securing applications in the context of Enterprise Mobility Management. Additionally, MAM solutions enable organizations to deploy, maintain, and manage both enterprise and third-party applications across their mobile estate. This capability ensures that business applications containing sensitive data remain secure while also delivering productivity applications required for users.
Mobile Content Management (MCM)
The third pillar of Enterprise Mobility Management is secure content sharing and collaboration. MCM solutions offer encrypted file sharing, document synchronization, and security-compliant collaborative workspaces. Further, these systems guarantee security for enterprise documents, wherever the location of the device and patterns of user access.
Mobile Identity Management (MIM)
Identity management in Enterprise Mobility Management solutions ensures that only those users who are approved can access business assets. MIM solutions are also combined with existing directory services and offer single sign-on for mobile applications and services.
Benefits of Implementing Enterprise Mobility Management
Organizations that deploy comprehensive Enterprise Mobility Management solutions experience significant advantages. First, enhanced security measures protect against data breaches and unauthorized access. Second, improved productivity results from streamlined device management and application deployment processes.
Additional benefits include
- Reduced IT support costs through automated management
- Enhanced compliance with regulatory requirements
- Improved user experience through self-service capabilities
- Better visibility into mobile device usage and security status
Best Practices for Enterprise Mobility Management Implementation
Successful deployment of EMM involves meticulous planning and implementation. Organizations initially need to perform a thorough inventory of existing mobile infrastructure and security needs. Then, establishing well-defined policies, along with procedures, ensures consistent deployment on every device and user.
Policy Formation
The development of detailed mobile device policies forms the basis of successful EMM. Policies have to cover device usage, app installation, data handling procedures, and security needs. In addition, periodic review of policies ensures compliance with changing security threats and business needs.
User Training and Support
Staff training is critical to the success of EMM Organizations need to conduct thorough training in security processes, acceptable use, and troubleshooting. Besides, continuous support allows the user to use EMM tools effectively while sustaining security processes.
Selecting the Proper Enterprise Mobility Management Solution
Choosing the ideal Enterprise Mobility Management platform involves critical assessment of organizational needs and technical requirements. Scalability, offering integration, security, and total cost of ownership are of greatest importance. Additionally, organizations need to assess vendor support, frequency of updates, and product roadmaps for the long term.
At Orasec, we understand the complexities of mobile security challenges in today’s era. With our cybersecurity expertise, organizations can implement efficient Enterprise Mobility Management solutions more easily that protect confidential information while allowing effective mobile working processes.
Future Directions in Enterprise Mobility Management
The Enterprise Mobility Management scenario keeps on changing with emerging trends and shifting work patterns. The adoption of artificial intelligence, zero-trust security models, and cloud-native architecture is transforming the EMM features. Furthermore, the growth of Internet of Things devices and edge computing adds new complexities and opportunities to mobile management platforms.
Conclusion
Enterprise Mobility Management is now a necessity for organizations that want to maximize mobility, productivity, and security. By adopting end-to-end EMM solutions that cover device management, application control, content security, and identity management, companies can safeguard their digital assets while enabling their people.
Ready to strengthen your business’s mobile security stance? Reach out to our cybersecurity professionals at Orasec to create a tailored Enterprise Mobility Management plan that is suitable for your individual business needs and security goals.