How Streamlining Penetration Testing Enhances Network Security
In today’s fast-changing digital landscape, cybersecurity is essential. As businesses adopt new technologies, their expanding digital infrastructure introduces vulnerabilities that cybercriminals exploit. This is where penetration testing (pen testing) steps in. However, it’s not just about conducting tests – the key is to optimize the process to safeguard systems efficiently without wasting resources.
The Growing Threat Landscape
As cyberattacks become more prevalent and regulatory demands grow, enterprises must show their dedication to preventing and addressing threats. By adopting a streamlined network penetration strategy, businesses can uncover and address vulnerabilities in their IT systems, safeguarding against breaches and enhancing brand trust. Continue reading to discover what penetration testing entails, the different types, and how to perform it
Fact: 71% of consumers steer clear of businesses that experience data breaches. Rebuilding trust is often more challenging than recovering from financial losses.
What exactly Penetration Testing is?
Pen testing is essentially “ethical hacking.” Penetration testing helps an organization discover vulnerabilities and flaws in their systems that they might not have otherwise been able to find. This can help stop attacks before they start, as organizations can fix these vulnerabilities once they have been identified.
Think of it as stress testing your system to ensure that no cracks go unnoticed. These simulated attacks are performed by ethical hackers (also known as white-hat hackers) who attempt to:
- Expose vulnerabilities
- Test security protocols
- Simulate internal and external breaches
- Provide actionable feedback
The goal? To uncover risks before they become problems.
Goal: Uncover and resolve vulnerabilities before they escalate into real threats.
Pentester’s simulation:
- External Attacks (as if they’re outsiders)
- Internal Breaches (assuming access from within)
Why Streamlining Pen Testing Matters
In the case of sporadic and inefficient penetration testing, this is like locking the front door but leaving the windows wide open. Testing for security must be continuous, efficient, and focused if it is to remain secure.
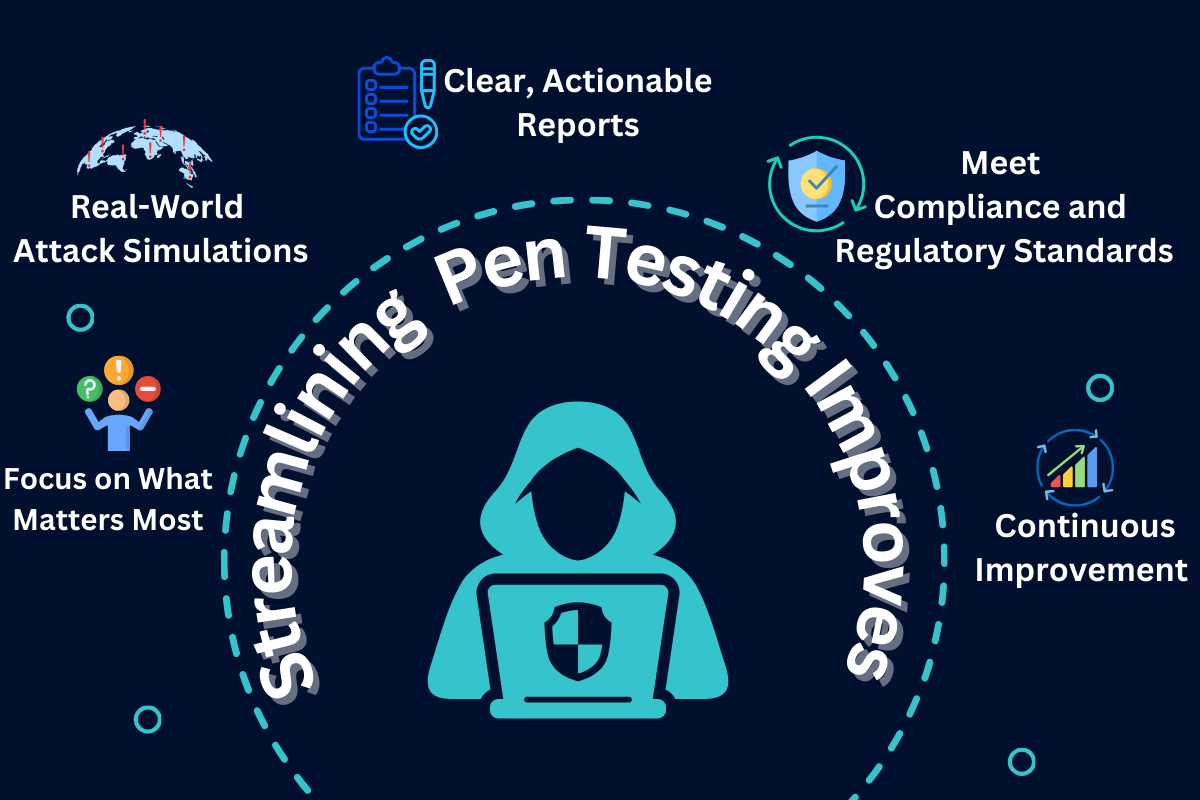
How Streamlining Pen Testing Improves Network Security
Focus on What Matters Most
Not all vulnerabilities are equal. Streamlined testing prioritizes the most critical threats first, ensuring the biggest risks are neutralized immediately. This smart allocation of resources prevents small issues from becoming massive headaches.
Continuous Improvement
Cyber threats evolve daily. A “one-and-done” pen test won’t cut it. By streamlining the process and making it regular, businesses continuously identify and fix new vulnerabilities that arise with changing technology.
Real-World Attack Simulations
By simulating real attacks repeatedly, businesses can verify whether their security fixes actually work. This approach ensures vulnerabilities don’t resurface and no new issues are inadvertently introduced.
📊 Clear, Actionable Reports
A streamlined pen testing process delivers clear, concise reports for leadership. By avoiding technical jargon, these reports explain cybersecurity risks in business terms, helping executives allocate resources and make informed decisions.
Meet Compliance and Regulatory Standards
Industries like healthcare, finance, and e-commerce face strict regulatory requirements (e.g., HIPAA, PCI-DSS). Regular penetration testing keeps businesses compliant, avoiding legal trouble and hefty fines.
The Business Case for Pen Testing
Beyond cybersecurity, penetration testing directly supports business continuity. By identifying vulnerabilities early, companies reduce downtime, protect critical systems, and avoid disruptions that could cost thousands—or millions—in lost revenue.
Pen Testing types (choose the right path)
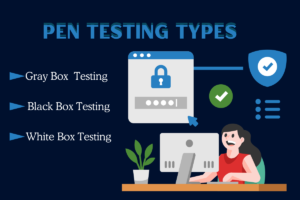
- Black Box Testing: Simulates an outsider attack with no prior knowledge of your systems.
- Gray Box Testing: Testers have partial access, mimicking an insider threat or compromised account.
- White Box Testing: The most in-depth, where testers have full system access, offering the most comprehensive evaluation.
Key Benefits of Streamlining Pen Testing
- Uncover Hidden Weaknesses: Test systems that often go unnoticed.
- Validate Security Measures: Confirm if existing defenses work.
- Build client and stakeholder trust: show commitment to safeguarding data.
- Maintain Regulatory Compliance: Avoid penalties and legal risks.
- Increase ROI: prevent breaches that could devastate finances.
How to Streamline Your Pen Testing Approach
- Set clear objectives: Define goals based on business needs and known vulnerabilities.
- Active Scanning and Reconnaissance: continuously scan for weak points, as hackers do.
- Simulate Attacks: Launch controlled cyberattacks to test defenses.
- Report and Act: Address vulnerabilities promptly, guided by detailed reports.
Why is it important to invest in pentesting now?
Penetration testing isn’t just about patching holes—it’s about building confidence. By proactively identifying and addressing vulnerabilities, companies can:
- Safeguard sensitive data
- Avoid financial losses
- Improve customer trust
Pentesting isn’t just about finding problems—it’s about preventing them. By identifying and addressing vulnerabilities, businesses protect their reputation, customers, and bottom line.
In today’s digital world, strong cybersecurity sets companies apart. Businesses prioritizing pen testing demonstrate leadership and commitment to protecting client data.