Microsoft Remote Desktop Protocol Under Siege: 30,000+ IP Addresses Target Critical Services
A vast synchronized scanning initiative aimed at Microsoft Remote Desktop Protocol (RDP) services, where malicious actors are using more than 30,000 distinct IP addresses to search for weaknesses in Microsoft RD Web Access and RDP Web Client login interfaces.
The campaign signifies one of the most extensive coordinated RDP reconnaissance efforts seen in recent years, indicating possible readiness for significant credential-based assaults.
Remote Desktop Protocol Attack Campaign
The scanning activity commenced with an initial surge on August 21, 2025, simultaneously involving almost 2,000 IP addresses directed at both Microsoft RD Web Access and Microsoft RDP Web Client services.
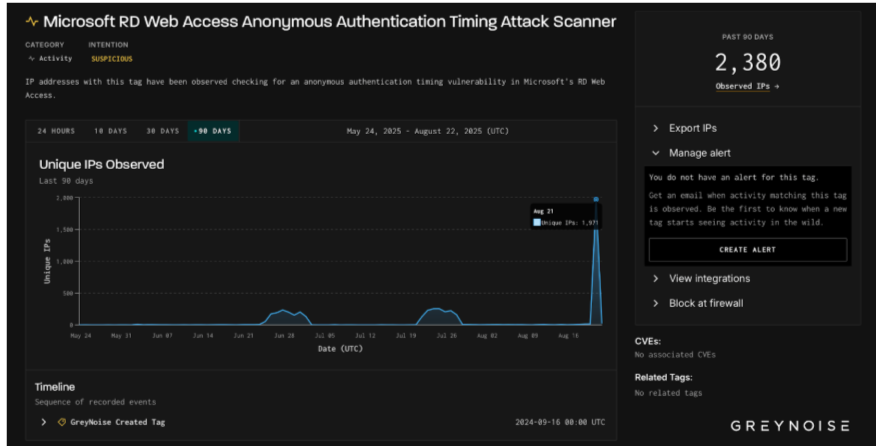
However, the campaign escalated dramatically on August 24, when security researchers detected over 30,000 unique IP addresses conducting coordinated probes using identical client signatures, indicating a sophisticated botnet infrastructure or coordinated toolset deployment.
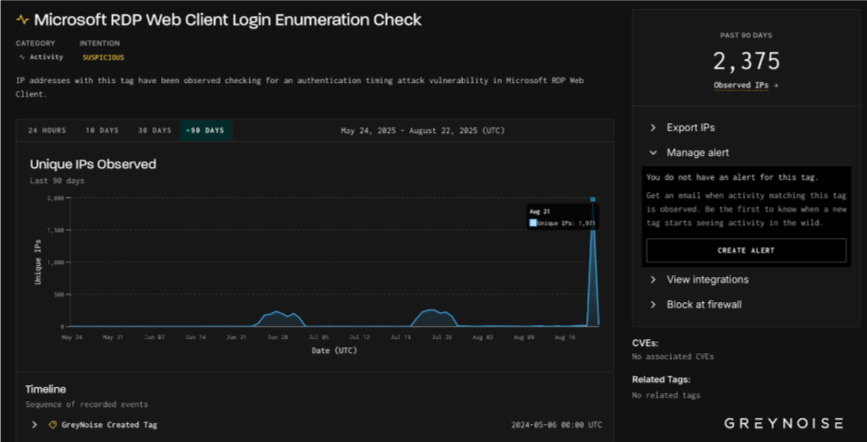
According to GreyNoise, the attack tactic is centered on timing-based authentication enumeration, which finds legitimate usernames without using conventional brute-force detection methods by taking advantage of minute variations in server response times.
By using this method, attackers can remain operationally stealthy while creating extensive target lists for upcoming credential stuffing and password spraying attacks.
According to network telemetry analysis, 92% of the scanning infrastructure is made up of malicious IP addresses that have already been categorized. Source traffic is mostly focused in Brazil (73% of observed sources), and it only targets RDP endpoints located in the United States.
A centralized command and control infrastructure characteristic of advanced persistent threat (APT) operations is suggested by the consistent client signature patterns found on 1,851 of the 1,971 initial scanning hosts.
Understanding the Current RDP Threat Landscape
The Microsoft Remote Desktop Protocol is a foundation technology for remote access in global enterprise networks. Recently, however, intelligence suggests that cybercrooks have stepped up targeting activities dramatically. Furthermore, security researchers have reported a complex campaign starting in late August 2025, which represents an unprecedented level of coordinated reconnaissance.
The Scale of the Attack Campaign
Security professionals have noted some of the disturbing trends in this Microsoft Remote Desktop Protocol attack campaign:
First Wave: The attack began on 21st August, 2025 with the utilization of nearly 2,000 IP addresses
Massive Scale-Up: Through August 24, the campaign had already reached over 30,000 unique IP addresses
Geographic Distribution: Malicious traffic is 73% Brazilian, versus US-based systems
Infrastructure Analysis: 92% of scan IPs were previously flagged as malicious
Moreover, attackers are employing timing-based authentication enumeration attacks. This sophisticated technique takes advantage of nanosecond variations in server response times in a bid to guess valid usernames without triggering traditional brute-force detection.
Educational Sector: Primary Target During Critical Period
The strategic timing of this campaign of exploitation by Microsoft Remote Desktop Protocol aligns with the US back-to-school season. Therefore, the schools that are utilizing RDP-enabled lab environments are vulnerable to increased threats during this vulnerable time.
Why Schools May Be Appealing Targets
Educational networks provide a variety of attributes that are appealing to cybercriminals:
- Predictable username schemas (student IDs, firstname.lastname formats)
- Large-scale RDP deployments for remote learning
- Often, limited cybersecurity budgets and resources
- High-value data, including student records and research
Therefore, educational IT departments must implement immediate protective measures to safeguard their Microsoft Remote Desktop Protocol infrastructure.
Advanced Reconnaissance Techniques Being Deployed
Threat intelligence shows that attackers are conducting multi-stage attacks beyond simple port scanning. Apart from that, they are also testing authentication workflows for information disclosure vulnerabilities and building comprehensive target databases.
Client Signature Analysis
Security researchers have observed similar client signature patterns repeatedly on 1,851 of the first 1,971 scanning hosts. This recurrence indicates:
- Centralized command and control framework
- Sophisticated botnet deployment
- Incorporate a toolset distribution typical of advanced persistent threat (APT) campaigns
Moreover, we can see from historical analysis that coordinated scanning spikes are usually followed by zero-day vulnerability findings within six weeks, based on 80% correlation rates in previous threat intelligence research.
Critical Vulnerabilities in Microsoft Remote Desktop Protocol
Some of these established vulnerabilities remain actual threats to organizations running RDP services:
BlueKeep and Related Vulnerabilities
CVE-2019-0708, or the BlueKeep vulnerability, remains a high-priority bug. It reveals a remote code execution vulnerability, which allows attackers to execute arbitrary code with invalid credentials. Additionally, several associated bugs have been found that enhance the threat landscape.
Authentication Bypass Techniques
Attacks today involve advanced methods, including:
- Timing-based enumeration attacks
- Credential stuffing campaigns
- Password spraying attacks
- Session hijacking attempts
Hence, organizations must implement multi-layered defense to protect their Microsoft Remote Desktop Protocol deployments.
Essential Security Measures for RDP Protection
Organizations can significantly reduce their exposure risk by implementing comprehensive security controls:
Network-Level Protections
- Network Segmentation: Isolate RDP services from internet-facing networks
- VPN Requirements: Mandate VPN connectivity before RDP access
- IP Whitelisting: Restrict access to known, trusted IP addresses
- Port Changes: Move RDP from default port 3389 to non-standard ports
Authentication Enhancements
Strong authentication mechanisms are crucial for Microsoft Remote Desktop Protocol security:
- Multi-Factor Authentication (MFA): Implement mandatory 2FA/MFA
- Account Lockout Policies: Configure aggressive lockout thresholds
- Strong Password Requirements: Enforce complex password policies
- Regular Credential Rotation: Mandate periodic password changes
Monitoring and Detection
Continuous monitoring enables early threat detection:
- Failed Login Monitoring: Track and alert on authentication failures
- Connection Logging: Maintain detailed RDP session logs
- Behavioral Analytics: Implement user behavior monitoring
- Threat Intelligence Integration: Incorporate IOC feeds for proactive blocking
How OraSec Helps Organizations Defend Against RDP Attacks
A professional penetration testing service like OraSec is worth the investment to detect Microsoft Remote Desktop Protocol vulnerabilities before attackers exploit them. OraSec professional penetration testers conduct extensive testing that includes:
RDP Configuration Analysis: Evaluating security deployments and configurations
Authentication Testing: Quantifying the effectiveness of access controls
Network Exposure Analysis: Identification of internet-exposed RDP services
Vulnerability Scanning: Detection of known and unknown security vulnerabilities
Their tailored solution gives businesses actionable insight applicable to their Microsoft Remote Desktop Protocol implementations. As an added value, OraSec provides in-depth remediation recommendations to harden defenses against emerging threats.
Conclusion and Call to Action
The ongoing Microsoft Remote Desktop Protocol exploitation campaign is one of the largest coordinated attacks seen in recent times. With over 30,000 persistent IP addresses probing weaknesses, organizations just cannot afford to wait to implement countermeasures. Security groups must check their RDP installations simultaneously, have multi-layered protection, and establish continuous monitoring capabilities.
One should also consider engaging expert cybersecurity providers such as OraSec to conduct detailed penetration testing and vulnerability scanning. The time is now—before attackers advance from reconnaissance to active exploitation. Harden your Microsoft Remote Desktop Protocol infrastructure today to safeguard your organization’s future.
