NOC vs. SOC: Why a Security Operations Center Is the Better Choice for Cybersecurity
Introduction
In the modern digital era, organizations are confronted with an even more difficult choice: whether to implement a Security Operations Center or a Network Operations Center to achieve complete cybersecurity protection. Both play significant roles in the running of IT infrastructure, but it is essential to know what each does to make the right choices. This comparison explains why a Security Operations Center is better for organizations that value strong cybersecurity defenses.
Understanding the Fundamental Differences
What Is a Network Operations Center (NOC)?
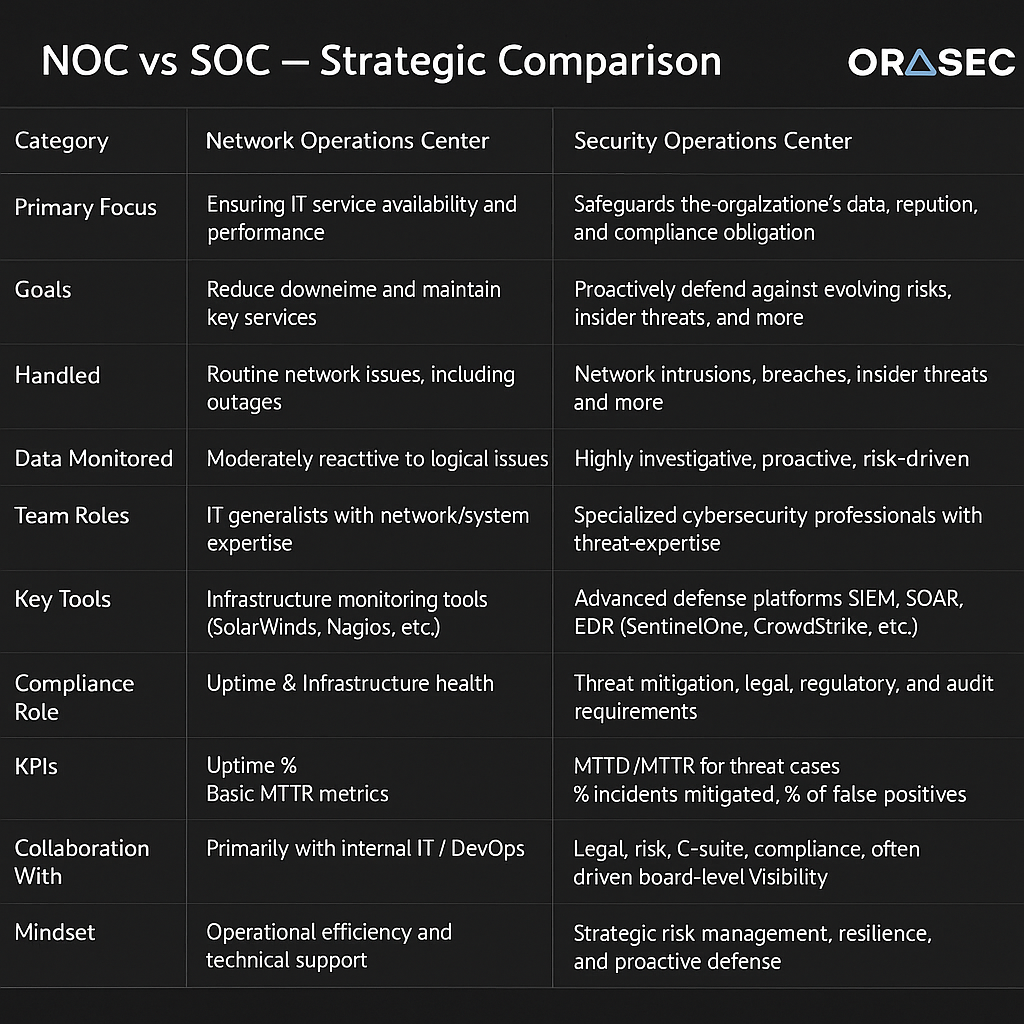
A Network Operations Center is primarily responsible for maintaining the network infrastructure up and running and offering optimum performance. Besides, NOC teams monitor network health, manage bandwidth, and resolve connectivity issues. But their domain extends to operational issues and not security-themed threats.
What is a Security Operations Center (SOC)?
Conversely, a Security Operations Center has one purpose only: cybersecurity monitoring, threat detection, and incident response. Furthermore, SOC analysts also use sophisticated security solutions and threat intelligence to detect malicious activity. Additionally, they deliver 24/7 security monitoring that responds to today’s ongoing cyber threats.
Why Security Operations Centers Excel in Modern Cybersecurity
Advanced Threat Detection Capabilities
Security Operation Centers employ next-generation security information and event management (SIEM) systems. Consequently, they can correlate security events from various sources and identify advanced attack patterns. Moreover, machine learning algorithms enhance their detection of zero-day threats and advanced persistent threats (APTs).
Expert Security Specialization
SOC analysts have expert-level cyber certifications and training. They are also aware of the latest threat profiles, attack vectors, and defense mechanisms. They are also expert-level in forensic analysis, malware analysis, and incident containment processes.
Proactive Threat Hunting
Unlike reactive NOC tactics, Security Operations Centers employ proactive threat hunting practices. They then actively search for indicators of compromise (IOCs) and possible security vulnerabilities. This proactive approach significantly reduces dwell time and reduces possible cyber attack damage.
Orasec: The Leading Security Operations Center Solutions
Orasec is a security operations center as a service pioneer delivering full-cycle cybersecurity solutions for businesses today. Their experienced experts offer 24/7 security monitoring, advanced threat detection, and real-time incident response capabilities. Orasec’s SOC-as-a-Service solution also offers cost-effective enterprise-class security operations without requiring enormous infrastructure spending.
Key Advantages of Choosing a Security Operations Center
Extended Security Monitoring
Security Operations Centers provide real-time monitoring of security events, network traffic, and system activity. They also provide granular security logs and forensic capabilities for incident post-mortem analysis. With this end-to-end approach, no security incident is ever left behind.
Rapid Incident Response
Whenever security incidents take place, SOC teams perform pre-defined incident response processes. They also contain the incidents, assess the damage, and execute recovery processes. Their quick response reduces business impact and recovery time.
Regulatory Compliance Support
Most industries have industry-specific cybersecurity compliance regulations. For this reason, Security Operations Centers assist organizations in attaining compliance with regulations via adequate documentation, audit trails, and enforcement of security controls. Such assistance is priceless when it comes to compliance posture.
COST-EFFECTIVE SECURITY OPERATIONS
Building an internal security operations capability requires significant investment in technology, personnel, and training. Managed SOC services, though, deliver enterprise-grade security operations for a fraction of the expense of building internally. This cost-effectiveness makes SOCs an attractive option for organizations of all sizes.
When NOCs Fall Short in Cybersecurity
Limited Security Focus
Network Operations Centers focus mainly on availability and performance concerns and not so much on security threats. They might thus overlook advanced attacks that do not immediately affect network performance. This weakness leaves perilous security vulnerabilities in an organization’s defense scheme.
Reactive Approach Limitations
NOCs usually act on problems after they have appeared as operational issues. Security threats, however, need to be identified and addressed proactively before they harm. This passive mode is not effective against contemporary cyber attacks.
Inadequate Security Tools
NOC environments usually do not have dedicated security tools such as SIEM systems, threat intelligence platforms, and forensic analysis. As a result, they are unable to offer the level of security analysis that is needed for successful threat detection and response.
Making the Correct Decision for Your Organization
Determining Your Security Needs
Organizations need to determine their individual security requirements, regulatory compliance needs, and tolerance for risk. In addition, take into account data asset sensitivity and the possible effects of security incidents. This analysis directs the decision between NOC and Security Operations Center deployments.
Considering Resource Availability
Take into consideration accessible budget, staff ability, and technical skill levels in your organization. Also, determine whether developing internal security operations capabilities supports strategic goals. Most organizations determine that managed SOC services yield the best value and expertise.
Planning for Future Growth
Security Operations Centers are scalable and flexible to meet changing threat patterns. In addition, they open access to new security technologies and methods without the need for internal development resources. This strategic thinking allows for long-term security effectiveness.
Conclusion
The decision to have an NOC or a Security Operations Center finally rests with organizational priorities and security needs. Nonetheless, with the advanced cyber threat landscape of the day, Security Operations Centers offer better protection through expert knowledge, cutting-edge tools, and proactive threat detection features. Organizations looking for all-around cybersecurity protection should give the highest priority to SOC deployments or managed SOC services such as those offered by Orasec.
Ready to enhance your cybersecurity posture? Consider implementing a Security Operations Center solution that addresses your specific security requirements and provides the robust protection your organization deserves.
FAQ Section:
1. What is the greatest difference between NOC and SOC?
A Network Operations Center (NOC) is concerned with monitoring network infrastructure and performance, whereas a Security Operations Center (SOC) is concerned with monitoring for cybersecurity threats, monitoring, and responding to incidents. SOCs have dedicated security professionals who are not found in NOCs.
2. Can a NOC manage cybersecurity tasks?
Although NOCs can detect some network-specific security problems, they do not have specialized security tools, know-how, and procedures for an all-encompassing cybersecurity defense. Organizations require specialized SOC capabilities for efficient threat detection and reaction.
3. Is it economically viable to set up a Security Operations Center?
Managed SOC services provide economically viable access to enterprise-class security operations without large infrastructure investments. This model offers a superior return on investment compared to establishing internal security operations capabilities from scratch.
4. How is Orasec’s SOC service advantageous to organizations?
Orasec offers 24×7 security monitoring, sophisticated threat detection, and swift incident response via their managed SOC solutions. Their presence ensures that organizations enjoy a strong cybersecurity stance while lessening operational cost and complexity.
5. When would an organization opt for SOC instead of NOC?
Organizations need to give SOC deployment top priority when they manage sensitive information, are subject to regulatory compliance mandates, or work in high-risk business sectors. Any organization that takes cybersecurity protection seriously profits from specialized SOC capabilities over depending solely on NOC operations.
